The company has enabled password reset through OW
###BeginCaseStudy###
Case Study: 13
Enterprise Company
Scenario:
Background
You are the desktop support technician for an enterprise company. The company offices,
sizes, and platforms are shown in the following table.
The Beijing office has been experiencing remote access issues. The company’s client
computers run Windows Vista and Windows 7. The company is in the process of upgrading
the Windows Vista client computers to Windows 7. All client computers have two volumes,
as shown in the following table.
The company’s password policy is shown in the following table.
The company’s account lockout policy is shown in the following table.
Software Environment
• The company has a single Active Directory Domain Services (AD DS) forest with
one domain. All domain controllers run Windows Server 2008 R2. The forest and domain
functional levels are set to Windows Server 2008 R2.
• The company outsources sales support to a third party.
• Each member of the Sales Support team has an AD DS user account in a global
security group named Sales.
• The Sales security group and the AD DS user accounts for the Sales Support team
reside in an organizational unit (OU) named Sales Support.
• Members of the Sales Support team do not use domain-joined client computers.
• With the exception of the Sales Support team, all user accounts reside in an OU
named Employees.
• All client computers reside in an OU named Client Computers.
• A global security group named Accounting contains users with domain accounts.
They use portable computers running Windows 7 that are joined to the domain.
• The company uses DirectAccess for remote access connectivity. Windows 7 domainjoined computers have been configured to use DirectAccess.
• The company uses Microsoft Exchange and Outlook Web App (OWA) for email and
collaboration. The company has enabled password reset through OWA.
The company uses AppLocker to prevent users from running certain programs. AppLocker
rules are defined at the domain-level in the Corp Group Policy object (GPO). Corp GPO only
contains AppLocker policy settings.
Wireless Requirements
The company has wireless access points (WAPs) that provide wireless connectivity at some
locations. The company uses a GPO named WiFi to enforce wireless security. The WiFi GPO
is linked to the domain. The company mandates that all domain-joined computers must
connect to corporate WAPs automatically. The company’s 802.1 X authentication server must
be used for client computer connections to the WAP. Visitors and contractors are unable to
connect to the corporate wireless network. Management has mandated that a guest wireless
network be established that meets the following criteria:
• Users should not have to provide credentials.
• Maximize wireless network performance.
• Minimize administrative overhead.
Data Protection Environment
• Full system backups are performed on client computers on Sundays with one week of
retention.
• All client computers are configured with System Protection settings to restore only
previous versions of files.
###EndCaseStudy###
You deploy a WAP in the company’s Beijing office. Client computers connect to it by using the WiFi
GPO. You deploy an 802.IX authentication server that is used to authenticate wireless connections.
You need to ensure that the wireless authentication meets the company’s requirements. Which
security option should you configure the wireless connections to use?
The company has enabled password reset through OW
###BeginCaseStudy###
Case Study: 13
Enterprise Company
Scenario:
Background
You are the desktop support technician for an enterprise company. The company offices,
sizes, and platforms are shown in the following table.
The Beijing office has been experiencing remote access issues. The company’s client
computers run Windows Vista and Windows 7. The company is in the process of upgrading
the Windows Vista client computers to Windows 7. All client computers have two volumes,
as shown in the following table.
The company’s password policy is shown in the following table.
The company’s account lockout policy is shown in the following table.
Software Environment
• The company has a single Active Directory Domain Services (AD DS) forest with
one domain. All domain controllers run Windows Server 2008 R2. The forest and domain
functional levels are set to Windows Server 2008 R2.
• The company outsources sales support to a third party.
• Each member of the Sales Support team has an AD DS user account in a global
security group named Sales.
• The Sales security group and the AD DS user accounts for the Sales Support team
reside in an organizational unit (OU) named Sales Support.
• Members of the Sales Support team do not use domain-joined client computers.
• With the exception of the Sales Support team, all user accounts reside in an OU
named Employees.
• All client computers reside in an OU named Client Computers.
• A global security group named Accounting contains users with domain accounts.
They use portable computers running Windows 7 that are joined to the domain.
• The company uses DirectAccess for remote access connectivity. Windows 7 domainjoined computers have been configured to use DirectAccess.
• The company uses Microsoft Exchange and Outlook Web App (OWA) for email and
collaboration. The company has enabled password reset through OWA.
The company uses AppLocker to prevent users from running certain programs. AppLocker
rules are defined at the domain-level in the Corp Group Policy object (GPO). Corp GPO only
contains AppLocker policy settings.
Wireless Requirements
The company has wireless access points (WAPs) that provide wireless connectivity at some
locations. The company uses a GPO named WiFi to enforce wireless security. The WiFi GPO
is linked to the domain. The company mandates that all domain-joined computers must
connect to corporate WAPs automatically. The company’s 802.1 X authentication server must
be used for client computer connections to the WAP. Visitors and contractors are unable to
connect to the corporate wireless network. Management has mandated that a guest wireless
network be established that meets the following criteria:
• Users should not have to provide credentials.
• Maximize wireless network performance.
• Minimize administrative overhead.
Data Protection Environment
• Full system backups are performed on client computers on Sundays with one week of
retention.
• All client computers are configured with System Protection settings to restore only
previous versions of files.
###EndCaseStudy###
Users in the Sales Support team access a web application that uses AD DS for authentication. Thirty
days after their user accounts are created users cannot authenticate to run the application. You
need to ensure that the Sales Support team can continue to use the web application. What should
you do?
The company has enabled password reset through OW
###BeginCaseStudy###
Case Study: 13
Enterprise Company
Scenario:
Background
You are the desktop support technician for an enterprise company. The company offices,
sizes, and platforms are shown in the following table.
The Beijing office has been experiencing remote access issues. The company’s client
computers run Windows Vista and Windows 7. The company is in the process of upgrading
the Windows Vista client computers to Windows 7. All client computers have two volumes,
as shown in the following table.
The company’s password policy is shown in the following table.
The company’s account lockout policy is shown in the following table.
Software Environment
• The company has a single Active Directory Domain Services (AD DS) forest with
one domain. All domain controllers run Windows Server 2008 R2. The forest and domain
functional levels are set to Windows Server 2008 R2.
• The company outsources sales support to a third party.
• Each member of the Sales Support team has an AD DS user account in a global
security group named Sales.
• The Sales security group and the AD DS user accounts for the Sales Support team
reside in an organizational unit (OU) named Sales Support.
• Members of the Sales Support team do not use domain-joined client computers.
• With the exception of the Sales Support team, all user accounts reside in an OU
named Employees.
• All client computers reside in an OU named Client Computers.
• A global security group named Accounting contains users with domain accounts.
They use portable computers running Windows 7 that are joined to the domain.
• The company uses DirectAccess for remote access connectivity. Windows 7 domainjoined computers have been configured to use DirectAccess.
• The company uses Microsoft Exchange and Outlook Web App (OWA) for email and
collaboration. The company has enabled password reset through OWA.
The company uses AppLocker to prevent users from running certain programs. AppLocker
rules are defined at the domain-level in the Corp Group Policy object (GPO). Corp GPO only
contains AppLocker policy settings.
Wireless Requirements
The company has wireless access points (WAPs) that provide wireless connectivity at some
locations. The company uses a GPO named WiFi to enforce wireless security. The WiFi GPO
is linked to the domain. The company mandates that all domain-joined computers must
connect to corporate WAPs automatically. The company’s 802.1 X authentication server must
be used for client computer connections to the WAP. Visitors and contractors are unable to
connect to the corporate wireless network. Management has mandated that a guest wireless
network be established that meets the following criteria:
• Users should not have to provide credentials.
• Maximize wireless network performance.
• Minimize administrative overhead.
Data Protection Environment
• Full system backups are performed on client computers on Sundays with one week of
retention.
• All client computers are configured with System Protection settings to restore only
previous versions of files.
###EndCaseStudy###
You plan to join Athens client computers to the AD DS domain. The Athens client computers connect
to the network via a wireless connection. You need to ensure that the Athens client computers can
be joined to the domain. What should you recommend?
The company has enabled password reset through OW
###BeginCaseStudy###
Case Study: 13
Enterprise Company
Scenario:
Background
You are the desktop support technician for an enterprise company. The company offices,
sizes, and platforms are shown in the following table.
The Beijing office has been experiencing remote access issues. The company’s client
computers run Windows Vista and Windows 7. The company is in the process of upgrading
the Windows Vista client computers to Windows 7. All client computers have two volumes,
as shown in the following table.
The company’s password policy is shown in the following table.
The company’s account lockout policy is shown in the following table.
Software Environment
• The company has a single Active Directory Domain Services (AD DS) forest with
one domain. All domain controllers run Windows Server 2008 R2. The forest and domain
functional levels are set to Windows Server 2008 R2.
• The company outsources sales support to a third party.
• Each member of the Sales Support team has an AD DS user account in a global
security group named Sales.
• The Sales security group and the AD DS user accounts for the Sales Support team
reside in an organizational unit (OU) named Sales Support.
• Members of the Sales Support team do not use domain-joined client computers.
• With the exception of the Sales Support team, all user accounts reside in an OU
named Employees.
• All client computers reside in an OU named Client Computers.
• A global security group named Accounting contains users with domain accounts.
They use portable computers running Windows 7 that are joined to the domain.
• The company uses DirectAccess for remote access connectivity. Windows 7 domainjoined computers have been configured to use DirectAccess.
• The company uses Microsoft Exchange and Outlook Web App (OWA) for email and
collaboration. The company has enabled password reset through OWA.
The company uses AppLocker to prevent users from running certain programs. AppLocker
rules are defined at the domain-level in the Corp Group Policy object (GPO). Corp GPO only
contains AppLocker policy settings.
Wireless Requirements
The company has wireless access points (WAPs) that provide wireless connectivity at some
locations. The company uses a GPO named WiFi to enforce wireless security. The WiFi GPO
is linked to the domain. The company mandates that all domain-joined computers must
connect to corporate WAPs automatically. The company’s 802.1 X authentication server must
be used for client computer connections to the WAP. Visitors and contractors are unable to
connect to the corporate wireless network. Management has mandated that a guest wireless
network be established that meets the following criteria:
• Users should not have to provide credentials.
• Maximize wireless network performance.
• Minimize administrative overhead.
Data Protection Environment
• Full system backups are performed on client computers on Sundays with one week of
retention.
• All client computers are configured with System Protection settings to restore only
previous versions of files.
###EndCaseStudy###
You need to troubleshoot the remote access issues in the Beijing office. What should you configure?
(Choose all that apply.)
Which Transact-SQL statement should you use?
You develop a Microsoft SQL Server 2012 server database that supports an application. The
application contains a table that has the following definition:
CREATE TABLE Inventory
(ItemID int NOT NULL PRIMARY KEY,
ItemsInStore int NOT NULL,
ItemsInWarehouse int NOT NULL)
You need to create a computed column that returns the sum total of the ItemsInStore and
ItemsInWarehouse values for each row.
Which Transact-SQL statement should you use?
You need to improve the performance of the view by persisting data to disk
You need to store the departure and arrival dates and times of flights along with time zone information
You develop a database for a travel application. You need to design tables and other database
objects.
You create the Airline_Schedules table.
You need to store the departure and arrival dates and times of flights along with time zone
information.
What should you do?
You need to supply the stored procedure with multiple event names and their dates as parameters
You develop a database for a travel application. You need to design tables and other database
objects. You create a stored procedure. You need to supply the stored procedure with multiple
event names and their dates as parameters. What should you do?
Which code segment should you use?
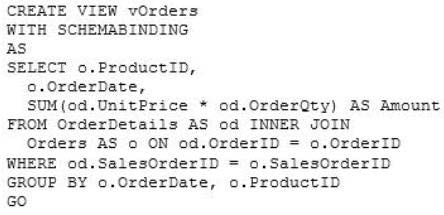
CORRECT TEXT
You have a view that was created by using the following code:
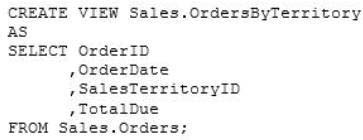
You need to create an inline table-valued function named Sales.fn_OrdersByTerritory, which must
meet the following requirements:
Accept the @T integer parameter.
Use one-part names to reference columns.
Filter the query results by SalesTerritoryID.
Return the columns in the same order as the order used in OrdersByTerritoryView.
Which code segment should you use?
To answer, type the correct code in the answer area.
Which code segment should you use?
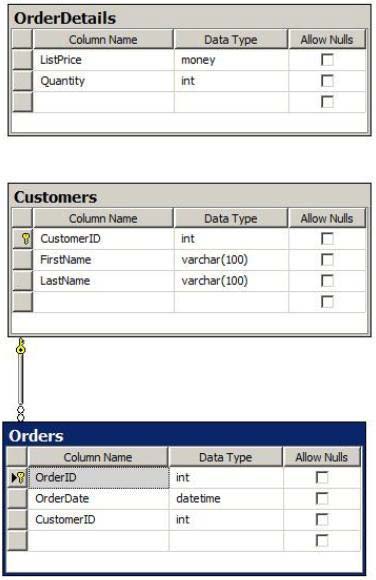
CORRECT TEXT
You have a database that contains the tables shown in the exhibit. (Click the Exhibit button.)
You deploy a new server that has SQL Server 2012 installed. You need to create a table named
Sales.OrderDetails on the new server. Sales.OrderDetails must meet the following requirements:
Write the results to a disk.
Contain a new column named LineItemTotal that stores the product of ListPrice and Quantity for
each row.
The code must NOT use any object delimiters.
The solution must ensure that LineItemTotal is stored as the last column in the table. Which code
segment should you use?
To answer, type the correct code in the answer area.