You need to configure the environment
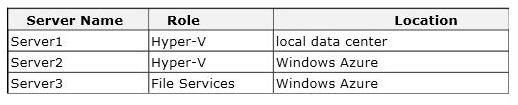
You administer three Windows Server 2012 R2 servers named Server1, Server2, and Server3. The
servers are configured as follows:
Each virtual machine on Served has a 50-TB logical unit number (LUN) to store data. There is limited
bandwidth between the local data center and Windows Azure.
You have the following business continuity requirements:
Virtual machines (VMs) on Server1 must be available within 30 minutes of an unexpected failure.
VMs on Server1 must be available if the local datacenter is no longer available.
You need to configure the environment. What should you do?
What should you deploy?
A company has Active Directory Domain Services (AD DS) domain controllers that run on Windows
Server 2012 R2 servers. There are two forests, and each has a single domain. There is a two-way
forest trust between the forests. The company uses Hyper-V for server visualization. The Hyper-V
environment contains the Hyper-V host servers as shown in the following table:
You prepare to deploy System Center 2012 R2 Data Protection Manager (DPM) to back up the
Hyper-V environment. The deployment must meet the following requirements:
ensure that all Hyper-V servers can be backed up by using DPM
Hyper-v hosts in the perimeter network must use certificate-based authentication
Hyper-V hosts in the internal network must use Kerberos authentication
minimize the total number of DPM servers
You need to deploy DPM to the environment.
What should you deploy?
Which tool should you use as part of the monitoring strategy?
A company has an environment that runs System Center 2012 R2 Operations Manager and System
Center 2012 R2 Virtual Machine Manager (VMM). The company also has web applications that are
used by employees.
You must plan a management strategy for the company.
You need to ensure that you can monitor the web applications from outside the company network.
Which tool should you use as part of the monitoring strategy?
You need to automate the process of adding the 20 new VMs to ProtectionGroup3
A company uses Windows Server 2012 R2 servers that have the Hyper-V role installed. The company
uses a single System Center 2012 R2 Data Protection Manager (DPM) server to back up and recover
the Hyper-V environment.
You deploy a new standalone Hyper-V host server, and then deploy 20 new virtual machines (VMs)
to the host server. You create a DPM protection group named ProtectionGroup3.
You need to automate the process of adding the 20 new VMs to ProtectionGroup3.
What should you run?
You need to monitor long-running SQL Server Agent jobs
You use System Center 2012 R2 Operations Manager to monitor the datacenter infrastructure and
applications for an organization. You import the SQL Server Management Pack.
You are unable to monitor long-running SQL Server Agent jobs. You observe that the SQL Server
Agent Jobs View displays zero instances Other SQL Server-related monitoring operations function as
expected.
You need to monitor long-running SQL Server Agent jobs.
What should you do?
You need to ensure that the username and password values are encrypted when they are deployed
You are developing a project that contains multiple SQL Server Integration Services (SSIS)
packages. The packages will be deployed to the SSIS catalog. One of the steps in each
package accesses an FTP site to download sales transaction data.
You create project parameters to store the username and password that are used to access
the FTP site.
You need to ensure that the username and password values are encrypted when they are
deployed.
What should you do?
You need to ensure that more accurate matches are made by the Fuzzy Lookup transformation without degrading pe
You develop a SQL Server Integration Services (SSIS) package that imports SQL Azure
data into a data warehouse every night.
The SQL Azure data contains many misspellings and variations of abbreviations. To import
the data, a developer used the Fuzzy Lookup transformation to choose the closest-matching
string from a reference table of allowed values. The number of rows in the reference table is
very large.
If no acceptable match is found, the Fuzzy Lookup transformation passes a null value.
The current setting for the Fuzzy Lookup similarity threshold is 0.50.
Many values are incorrectly matched.
You need to ensure that more accurate matches are made by the Fuzzy Lookup
transformation without degrading performance.
What should you do?
You need to create the SSIS catalog on the production server
You install a SQL Server 2012 database engine instance on a production server. A month
later, you install SQL Server 2012 Integration Services (SSIS).
You must develop an SSIS project and deploy it to the server by using the Project
Deployment model.
Operations Log records that are outside the configured retention period must be cleaned
automatically.
You need to create the SSIS catalog on the production server.
What should you do? (Each correct answer presents part of the solution. Choose all that
apply.)
Where can you find this information?
A SQL Server Integration Services (SSIS) package on a computer is failing periodically in
production. The package was created less than one year ago and was deployed to the SSIS
catalog.
Sometimes the package is started on a SQL Agent schedule; sometimes the package is
started manually by an SSIS developer by using the Object Explorer in SQL Server
Management Studio.
You need to identify the authenticated user responsible for starting the package each time it
failed in the past.
Where can you find this information?
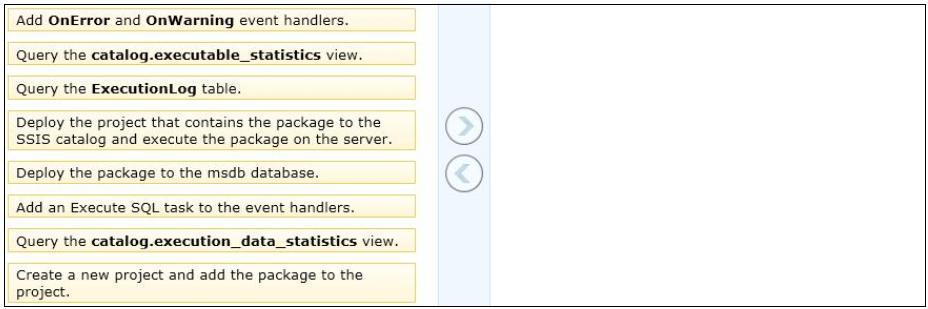
Which three actions should you perform in sequence?
DRAG DROP
A SQL Server Integration Services (SSIS) package named DataFeed interacts with an
external vendor data feed. The package is executed several times a day, either as part of
other packages’ control flow or by itself. The external data feed is unreliable because
network failures and slow response times are frequent. The package is currently deployed
on the file system.
To analyze the reliability of the external data feed, you must collect execution data.
Every time the DataFeed package is executed, the following information must be logged:
Start Time
End Time
Execution Result
Execution Duration
You need to design a logging solution that meets the requirements by using the least
amount of administrative and development effort.
Which three actions should you perform in sequence? (To answer, move the appropriate
actions from the list of actions to the answer area and arrange them in the correct order.)