Which two actions should you perform?
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
You need to ensure that a WIM file that is located on a network share is used as the installation
source when installing server roles and features on Server1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose
two.)
Which three actions should you perform?
Yournetwork contains an Active Directory forest.
The forest contains two domains named contoso.com and fabrikam.com.
The functional level of the forest is Windows Server 2003.
Youhave a domain outside the forest named litwareinc.com.
Youneed to configure an access solution to meet the following requirements:
Users in litwareinc.com must be able to access resources on a server named Server1 in
contoso.com.
Users in the contoso.com forest must be prevented from accessing any resources in
litwareinc.com.
Users in litwareinc.com must be prevented from accessing any other resources in the
contoso.com forest.
Which three actions should you perform? (Each correct answer presents part of the solution.
Choose three.)
Which two actions should you perform?
Yournetwork contains an Active Directory domain named contoso.com.
The domain contains two domain controllers named DC1 and DC2 that run Windows Server 2012
R2.
DC1 and DC2 fail to replicate Active Directory information.
Youconfirm that DC1 and DC2 have network connectivity.
The NTDS Settings of DC2 are configured as shown in the NTDS Settings exhibit. (Click tie Exhibit
button.)
DNS is configured as shown in the DNS exhibit. (Click the Exhibit button.)
You need to ensure that DC1 and DC2 can replicate immediately.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose
two.)
Which disk should you identify?
Your network contains an Active Directory domain named contoso.com.
The domain contains two member servers named Server1 and Server2.
All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature
installed.
The servers are configured as nodes in a failover cluster named Cluster1.
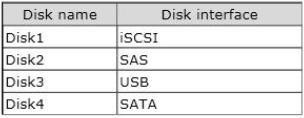
Cluster1 has access to four physical disks.
The disks are configured as shown in the following table.
You need to identify which disk can be added to a Clustered Storage Space in Cluster1.
Which disk should you identify?
You need to delete the is Confidential classification property
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has the File Server Resource Manager role service installed.
You attempt to delete a classification property and you receive the error message as shown in the
exhibit. (Click the Exhibit button.)
You need to delete the is Confidential classification property.
What should you do?
You need to ensure that the new RODC will be able to replicate from DC10
Your network contains an Active Directory domain named contoso.com.
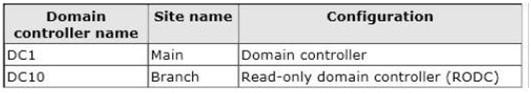
All domain controllers run Windows Server 2012 R2. The domain contains two domain controllers.
The domain controllers are configured as shown in the following table.
The Branch site contains a perimeter network.
For security reasons, client computers in the perimeter network can communicate with client
computers in the Branch site only.
You plan to deploy a new RODC to the perimeter network in the Branch site.
You need to ensure that the new RODC will be able to replicate from DC10.
What should you do first on DC10?
What should you do?
You have a server named LON-DC1 that runs Windows Server 2012 R2.
An iSCSI virtual disk named VirtuahSCSIl.vhd exists on LON-DC1 as shown in the exhibit. (Click the
Exhibit button.)
Youcreate a new iSCSI virtual disk named VirtualiSCSI2.vhd by using the existing itgt iSCSI target.
VirtualiSCSIl.vhd is removed from LON-DC1.
Youneed to assign VirtualiSCSI2.vhd a logical unit value of 0.
What should you do?
Which tool should you use?
Your network contains an Active Directory domain named contoso.com.
The domain contains two domain controllers named DC1 and DC2.
You install Windows Server 2012 R2 on a new computer named DC3.
You need to manually configure DC3 as a domain controller.
Which tool should you use?
Which tool should you use?
Yournetwork contain an active directory domain named Contoso.com.
The domain contains two servers named server1 and server2 that run Windows Server 2012 R2.
You create a security template named template1 by using the security template snap-in.
You need to apply template1 to server2.
Which tool should you use?
Which tool should you use?
Yournetwork contains an Active Directory forest named contoso.com.
All servers run Windows Server 2012 R2.
You need to create a custom Active Directory Application partition.
Which tool should you use?