What should you create?
Your network contains an Active Directory forest. The forest contains two domains named
contoso.com and fabrikam.com. The functional level of the forest is Windows Server 2003.
You have a domain outside the forest named adatum.com.
You need to configure an access solution to meet the following requirements:
* Users in adatum.com must be able to access resources in contoso.com.
* Users in adatum.com must be prevented from accessing resources in fabrikam.com.
* Users in both contoso.com and fabrikam.com must be prevented from accessing resources in
adatum.com.
What should you create?
Which tool should you use?
Your network contains an Active Directory forest named contoso.com. The forest contains a single
domain. The forest functional level is Windows Server 2012 R2.
You have a domain controller named DC1.
On DC1, you create a new Group Policy object (GPO) named GPO1. You need to verify that GPO1
was replicated to all of the domain controllers.
Which tool should you use?
Which tool should you use?
Your network contains an Active Directory forest named contoso.com. The forest contains a single
domain. The forest functional level is Windows Server 2012 R2.
You have a domain controller named DC1.
On DC1, you create a new Group Policy object (GPO) named GPO1. You need to verify that GPO1
was replicated to all of the domain controllers.
Which tool should you use?
Which two actions should you perform?
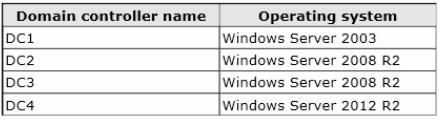
Your network contains an Active Directory forest named contoso.com. The forest contains two
domains named contoso.com and childl.contoso.com. The domains contain three domain
controllers. The domain controllers are configured as shown in the following table.
You need to ensure that the KDC support for claims, compound authentication, and kerberos
armoring setting is enforced in both domains.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose
two.)
Which tool should you use?
Your company recently deployed a new Active Directory forest named contoso.com. The forest
contains two Active Directory sites named Site1 and Site2. The first domain controller in the forest
runs Windows Server 2012 R2.
You need to force the replication of the SYSVOL folder from Site1 to Site2.
Which tool should you use?
Which tool should you use?
Your company recently deployed a new Active Directory forest named contoso.com. The forest
contains two Active Directory sites named Site1 and Site2. The first domain controller in the forest
runs Windows Server 2012 R2.
You need to force the replication of the SYSVOL folder from Site1 to Site2.
Which tool should you use?
What should you do?
Your network contains an Active Directory forest named contoso.com. The forest contains a single
domain. The forest contains three Active Directory sites named SiteA, SiteB, and SiteC. The sites
contain four domain controllers. The domain controllers are configured as shown in the following
table.
An IP site link exits between each site.
Youdiscover that the users in SiteC are authenticated by the domain controllers in SiteA and SiteB.
Youneed to ensure that the SiteC users are authenticated by the domain controllers in SiteB, unless
all of the domain controllers in SiteB are unavailable.
What should you do?
What should you do first?
Yournetwork contains an Active Directory forest. The forest contains one domain named
adatum.com. The domain contains three domain controllers. The domain controllers are configured
as shown in the following table.
DC2 has all of the domain-wide operations master roles. DC3 has all of the forest-wide operation
master roles.
Youneed to ensure that you can use Password Settings objects (PSOs) in the domain.
What should you do first?
What should you do?
Youhave a server named FS1 that runs Windows Server 2012 R2.
Youinstall the File and Storage Services server role on FS1.
From Windows Explorer,you view the properties of a shared folder named Share1 and you discover
that the Classification tab is missing.
Youneed to ensure that you can assign classifications to Share1 from Windows Explorer manually.
What should you do?
What should you do on Server1?
Yournetwork contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
Server1 and Server2 are configured as shown in the following table.
Youneed to ensure that when new targets are added to Server1, the targets are registered on
Server2 automatically.
What should you do on Server1?