hown in follow:- For each of the following statement…
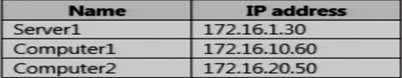
Your network contains an Active Directory named contoso.com.
The domain contains the computers configured as shown in the following table.
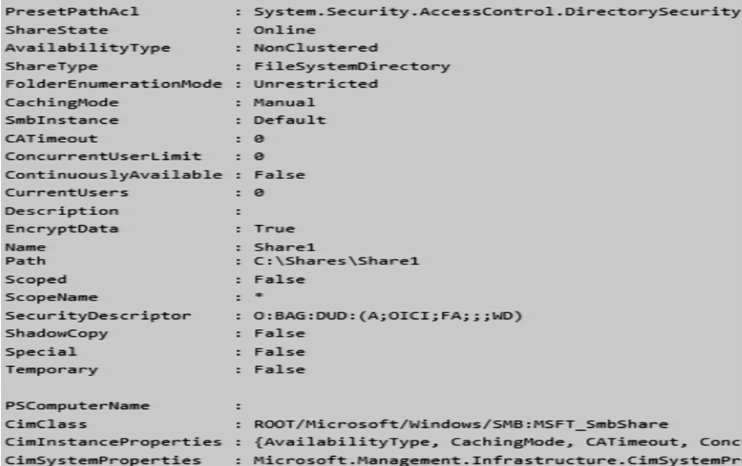
Server1 has a share named Share1 with the following configurations:-
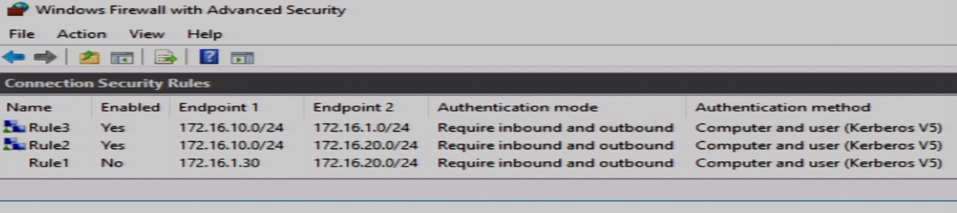
Server1, Computer1, and Computer2 have the connection security rules configured as shown in follow:-
For each of the following statements are true? Choose Three.
You need to import the security policy into SCM
Your network contains an Active Directory domain named contoso.com. The domain contains a DNS server
named Server1 that runs Windows Server 2016.
A domain-based Group Policy object (GPO) is used to configure the security policy of Server1.
You plan to use Security Compliance Manager (SCM) 4.0 to compare the security policy of Server1 to the
WS2012 DNS Server Security 1.0 baseline.
You need to import the security policy into SCM. What should you do first?1
Which two actions should you perform?
You have a Hyper-V host named Hyperv1 that has a virtual machine named FS1. FS1 is a file server that
contains sensitive data.
You need to secure FS1 to meet the following requirements:
-Prevent console access to FS1.
-Prevent data from being extracted from the VHDX file of FS1.
Which two actions should you perform? Each correct answer presents part of the solution.
How many OMS agents should you deploy?
You have the servers configured as shown in the following table.
You purchase a Microsoft Azure subscription, and you create three Microsoft Operations Management Suite
(OMS) workspaces named Workspace1, Workspace2,
and Workspace3
You need to deploy Microsoft Monitoring Agent to the servers to meet the following requirements:
-Antimalware data from all the servers must be visible in Workspace1.
-Security and audit data from the domain controllers and the virtualization hosts must be visible in Workspace2.
-System update data from all the servers in all the workgroups must be visible in Workspace&
How many OMS agents should you deploy?
What should you install on each server to ensure that t…
Your network contains an Active Directory domain named contoso.com. The domain contains multiple servers
that run either
Windows Server 2012 or Windows Server 2012 R2.
You plan to implement Just Enough Administration (JEA) to manage all of the servers.
What should you install on each server to ensure that the servers can be managed by using JEA?
What should you include in the recommendation?
Your network contains two single-domain Active Directory forests named contoso.com and contosoadmin.com.
Contosoadmin.com contains all of the user accounts used to manage the servers in contoso.com.You need to recommend a workstation solution that provides the highest level of protection from vulnerabilities
and attacks.
What should you include in the recommendation?
which group should you add Admin1?
Your network contains an Active Directory forest named contoso.com. All servers run Windows Server 2016.
You implement a single-domain administrative forest named admin.contoso.com that has Enhanced Security
Administrative Environment (ESAE) deployed.
You have an administrative user named Admin1 in admin.contoso.com.
You need to ensure that Admin1 can manage the domain controllers in contoso.com.
To which group should you add Admin1?
You need to ensure that the credentials that you use to…
You need to install the required server roles for the p…
Your data center contains 10 Hyper-V hosts that host 100 virtual machines.
You plan to secure access to the virtual machines by using the Datacenter Firewall service.
You have four servers available for the Datacenter Firewall service. The servers are configured as shown in the
following table.
You need to install the required server roles for the planned deployment
Which server role should you deploy? Choose Two.
What should you install on Server1?
Your network contains an Active Directory domain named contoso.com. The domain contains several shielded
virtual machines.
You deploy a new server named Server1 that runs Windows Server 2016. You install the Hyper-V server role
on Server1.
You need to ensure that you can host shielded virtual machines on Server1.
What should you install on Server1?