You need to apply this configuration to all virtual mac…
You manage an application that has a front-end tier, a middle tier, and a back-end tier. Each tier is located on a
different subnet.
You need to apply access to and between the tiers as follows:
Only the front-end tier must be able to access the Internet.
You must permit network access between the front-end tier and the middle tier.
You must permit network access between the middle tier and the back-end tier.
You must prevent all other network traffic.
You need to apply this configuration to all virtual machines inside the subnets.
What should you do?
Which actions should you perform?
How should you configure the command?
HOTSPOT
You are the administrator for your company’s Azure environment.
A developer creates an application that needs to access resources in external systems. The application will be
deployed in the domain.
You need to use the Azure Command-Line Interface (CLI) to create a service principal.
How should you configure the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Which three actions should you perform in sequence?
DRAG DROP
You have an Azure Subscription.
You have an on-premises site that contains a server named Server1. Server1 runs Windows Server 2012 R2
and has computer digital certificate named Cert1.
You need to ensure that you can back up Server1 to Azure.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of
actions to the answer area and arrange them in the correct order.
Select and Place:
How should you configure the environment?
HOTSPOT
You plan to deploy Ubuntu Linux virtual machines (VMs) in Azure.
You need to ensure that you are not prompted for a password when you create or connect to the Vms.
How should you configure the environment? To answer, configure the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Hot Area:
HOTSPOT
You manage a public-facing web application which allows authenticated users to upload and download large
files. On the initial public page there is a promotional video.
You plan to give authenticated users the ability to upload and download large files. Anonymous users should be
able to view the promotional video.
In the table below, identify the access method that should be used for the anonymous and authenticated parts
of the application.
Make only one selection in each column.
Hot Area:
what should you implement?
DRAG DROP
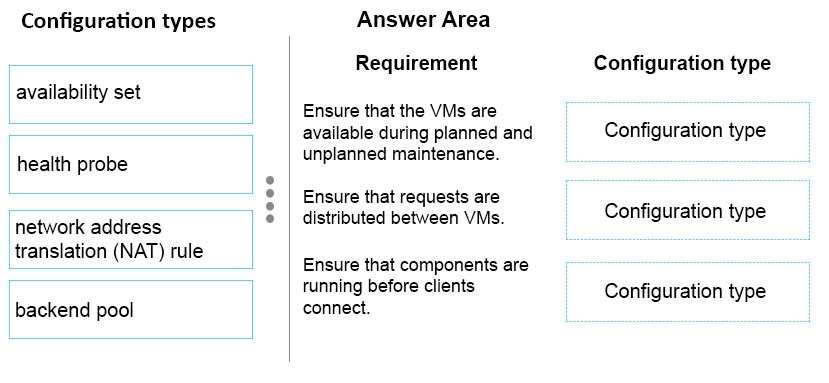
You plan to deploy an application by using three Azure virtual machines (VMs). The application has a webbased component that uses TCP port 443 and a custom component that uses UDP port 2020.
The application must be available during planned and unplanned Azure maintenance events. Incoming client
requests must be distributed across the three VMs. Clients must be connected to a VM only if both application
components are running.
You need to configure the VM environment.
For each requirement, what should you implement? To answer, drag the appropriate configuration type to the
correct target. Each configuration type may be used once, more than once, or not at all. You may need to drag
the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Which four Azure PowerShell cmdlets or scripts should y…
DRAG DROP
You are managing an Azure SQL Database.
You need to export the database to a BACPAC file and verify that the export completes successfully.
Which four Azure PowerShell cmdlets or scripts should you run in sequence? To answer, move the appropriate
cmdlets or scripts from the list of cmdlets to the answer area and arrange them in the correct order.
Select and Place:
What should you do?
You administer an Azure SQL Database that runs in the S0 service tier. The database stored mission-critical
data.
You must meet the following requirements:
minimize costs associated with hosting the database in Azure
minimize downtime in the event of an outage
protect the database from unplanned events
What should you do?
You need to ensure the new VMs can communicate with the…
You deploy several virtual machines (VMs) to Azure by using the Azure Service Manager (classic).
You must deploy new VMs by using the Azure Resource Manager (ARM).
You need to ensure the new VMs can communicate with the existing Vms.
What should you do?