Which tool should you use?
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has five network adapters.
Three of the network adapters are connected to a network named LAN1. The two other network adapters are
connected to a network named LAN2.
You need to create a network adapter team from the three network adapters connected to LAN1.
Which tool should you use?
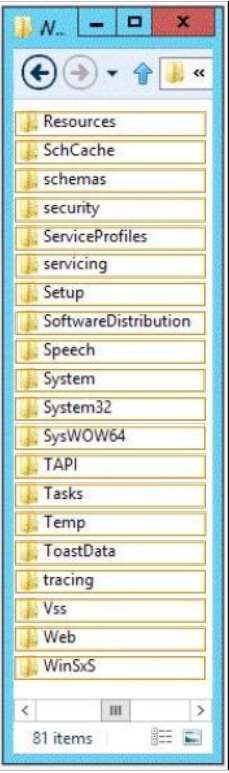
Which folder should you use as the source?
HOTSPOT
You have a server named Server1 that runs Windows Server 2012 R2. Server1 does not have Internet
connectivity.
All roles are removed completely from Server1.
You mount a Windows Server 2012 R2 installation image to the C:\\Source folder.
You need to install the DNS Server server role on Server1.
Which folder should you use as the source? To answer, select the appropriate folder in the answer area.
Hot Area:
Which type of group should you create?
Your network contains an Active Directory forest named contoso.com. The forest contains a child domain
named corp.contoso.com.
The network has Microsoft Exchange Server 2010 deployed.
You need to create a mail-enabled distribution group.
Which type of group should you create?
Which tool should you use?
Your network contains an Active Directory domain named contoso.com.
You discover that when you join client computers to the domain manually, the computer accounts are created in
the Computers container.
You need to ensure that new computer accounts are created automatically in an organizational unit (OU)
named Corp.
Which tool should you use?
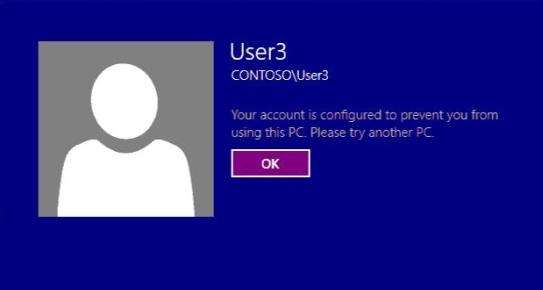
You need to ensure that User3 can log on to Client10
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012
R2.
When a domain user named User3 attempts to log on to a client computer named Client10, User3 receives the
message shown in the following exhibit. (Click the Exhibit button.)
You need to ensure that User3 can log on to Client10.
What should you do?
You need to ensure that a user named User1 can access Web1
Your network contains an Active Directory domain named contoso.com. The domain contains a server named
Server1 that runs Windows Server 2012 R2 and has the Web Server (IIS) server role installed.
Server1 has a web site named Web1. Web1 is configured to use digest authentication.
You need to ensure that a user named User1 can access Web1.
What should you do from Active Directory Users and Computers?
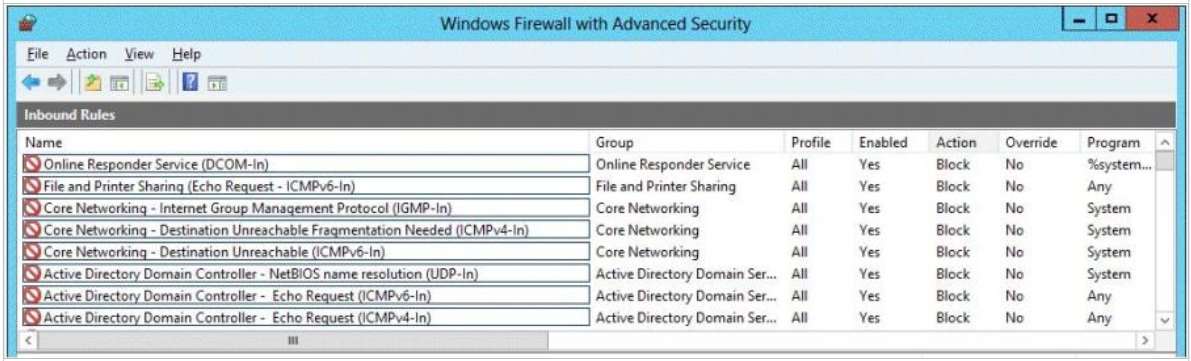
Which firewall rule should you modify on DC5?
HOTSPOT
Your network contains a domain controller named dc5.adatum.com that runs Windows Server 2012 R2.You discover that you can connect successfully to DC5 over the network, but you receive a request timed out
message when you attempt to ping DC5.
You need to configure DC5 to respond to ping request.
Which firewall rule should you modify on DC5? To answer, select the appropriate rule in the answer area.
Hot Area:
Which Diskpart command should you use?
You have a server named Server1 that runs a Server Core Installation of Windows Server 2012 R2. You attach
a 4-TB disk to Server1.
The disk is configured as an MBR disk. You need to ensure that you can create a 4-TB volume on the disk.
Which Diskpart command should you use?
What should you run on Server1?
You have a server named Server1 that runs Windows Server 2012 R2.
You need to remove Windows Explorer, Windows Internet Explorer, and all related components and files from
Server1.
What should you run on Server1?
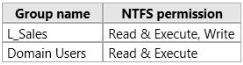
You need to ensure that the members of L_Sales can add …
You have a file server named File1 that runs Windows Server 2012 R2.
File1 contains a shared folder named Share1. Share1 contains an Application named SalesAppl.exe.
The NTFS permissions for Share1 are shown in the following table.
The members of L_Sales discover that they cannot add files to Share1. Domain users can run SalesAppl.exe
successfully.
You need to ensure that the members of L_Sales can add files to Share1.
What should you do?