Which two commands should you run from Windows PowerShell?
Your network contains an Active Directory domain named contoso.com. The domain contains a member server
named HVServer1. HVServer1 runs Windows Server 2012 R2 and has the Hyper-V server role installed.
HVServer1 hosts two virtual machines named Server1 and Server2. Both virtual machines connect to a virtual
switch named Switch1.
On Server2, you install a network monitoring application named App1.
You need to capture all of the inbound and outbound traffic to Server1 by using App1.
Which two commands should you run from Windows PowerShell? (Each correct answer presents part of the
solution. Choose two.)
Which two actions should you perform?
Your network contains a Hyper-V host named Hyperv1 that runs Windows Server 2012 R2.
Hyperv1 has a virtual switch named Switch1.You replace all of the network adapters on Hyperv1 with new network adapters that support single-root I/O
virtualization (SR-IOV). You need to enable SR-IOV for all of the virtual machines on Hyperv1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
What should you do for server core so it can be managed…
What should you create?
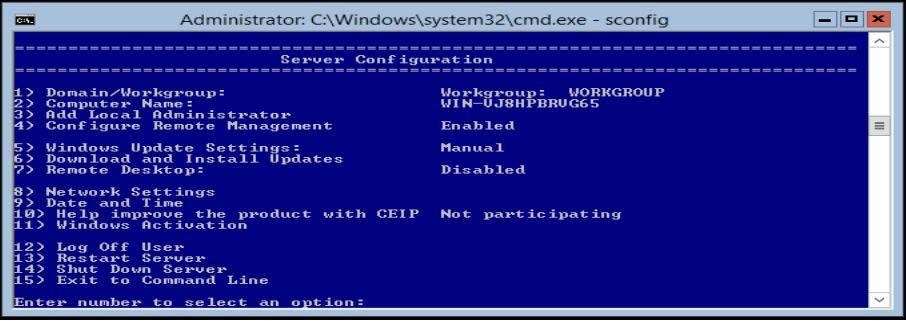
You have a server that runs Windows Server 2012 R2. The server contains the disks configured as shown in
the following table.
You need to create a volume that can store up to 3 TB of user files. The solution must ensure that the user files
are available if one of the disks in the volume fails.
What should you create?
You need to ensure that a user named User1 can link and…
Your network contains an Active Directory domain named contoso.com. The domain contains 100 user
accounts that reside in an organizational unit (OU) named 0U1. You need to ensure that a user named User1
can link and unlink Group Policy objects (GPOs) to OU1. The solution must minimize the number of
permissions assigned to User1.
What should you do?
You need to preventServer1 from attempting to resolve I…
Your network contains an Active Directory domain named contoso.com. The network contains 500 client
computers that run Windows 8. All of the client computers connect to the Internet by using a web proxy.
You deploy a server named Server1 that runs Windows Server 2012 R2. Server1 has the DNS Server server
role installed.
You configure all of the client computers to use Server1 as their primary DNS server. You need to preventServer1 from attempting to resolve Internet host names for the client computers.
What should you do on Server1?
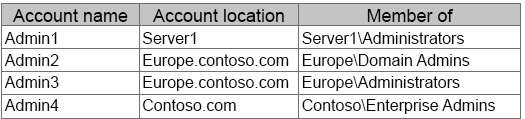
You have access to the administrative accounts shown …
Your network contains an Active Directory forest named contoso.com. The forest contains a child domain
named europe.contoso.com. The europe.contoso.com child domain contains a server named Server1 that runs
Windows Server 2012 R2. You install the DHCP Server server role on Server1. You have access to the
administrative accounts shown in the following table.
Which two actions should you perform?
You have a server named Server1. Server1 runs Windows Server 2012 R2 and has the File and Storage
Services server role installed. You attach four 500-GB disks to Server1. You need to configure the storage to
meet the following requirements:
Storage for an application named Application1 must be provided. Application1 requires 20 GB and will
require a maximum of 800 GB in three years.
Storage for an application named Application2 must be provided. Application2 requires 20 GB and will
require a maximum of 900 GB in three years.
The solution must provide the ability to dynamically add storage without requiring configuration changes to
the applications.
The storage must be available if a single disk fails.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
Which server role should you install on Server1?
Your network contains an active directory forest. The forest functional level is Windows server 2012. The forest
contains a single domain. The domain contains a member server named Server1 that runs Windows server
2012. You purchase a network scanner named Scanner1 that supports Web Services on Devices (WDS). You
need to share the network scanner on Server1.
Which server role should you install on Server1?
Which rule should you enable?
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 is located on the
same subnet as all of the client computers. A network technician reports that he receives a “Request timed out”
error message when he attempts to use the ping utility to connect to Server1 from his client computer. The
network technician confirms that he can access resources on Server1 from his client computer.
You need to configure Windows Firewall with Advanced Security on Server1 to allow the ping utility to connect.
Which rule should you enable?