Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series
contains a unique solution that might meet the stated goals. Some question sets might have more than one
correct solution, while others might not have a correct solution.
After you answer a question in this sections, you will NOT be able to return to it. As a result, these questions will
not appear in the review screen.
You are building a security tracking solution in Apache Kafka to parse security logs. The security logs record an
entry each time a user attempts to access an application. Each log entry contains the IP address used to make
the attempt and the country from which the attempt originated.
You need to receive notifications when an IP address from outside of the United States is used to access the
application.
Solution: Create a consumer and a broker. Create a file import process to send messages. Run the producer.
Does this meet the goal?
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series
contains a unique solution that might meet the stated goals. Some question sets might have more than one
correct solution, while others might not have a correct solution.
After you answer a question in this sections, you will NOT be able to return to it. As a result, these questions will
not appear in the review screen.
You are building a security tracking solution in Apache Kafka to parse security logs. The security logs record an
entry each time a user attempts to access an application. Each log entry contains the IP address used to make
the attempt and the country from which the attempt originated.
You need to receive notifications when an IP address from outside of the United States is used to access the
application.
Solution: Create new topics. Create a file import process to send messages. Start the consumer and run the
producer.
Does this meet the goal?
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in
the series contains a unique solution that might meet the stated goals. Some question sets might have
more than one correct solution, while others might not have a correct solution.
After you answer a question in this sections, you will NOT be able to return to it. As a result, these
questions will not appear in the review screen.
You are building a security tracking solution in Apache Kafka to parse security logs. The security logs record an
entry each time a user attempts to access an application. Each log entry contains the IP address used to make
the attempt and the country from which the attempt originated.
You need to receive notifications when an IP address from outside of the United States is used to access the
application.
Solution: Create two new consumers. Create a file import process to send messages. Start the producer.
Does this meet the goal?
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in
the series contains a unique solution that might meet the stated goals. Some question sets might have
more than one correct solution, while others might not have a correct solution.
After you answer a question in this sections, you will NOT be able to return to it. As a result, these
questions will not appear in the review screen.
You are building a security tracking solution in Apache Kafka to parse security logs. The security logs record an
entry each time a user attempts to access an application. Each log entry contains the IP address used to make
the attempt and the country from which the attempt originated.
You need to receive notifications when an IP address from outside of the United States is used to access the
application.
Solution: Create two new brokers. Create a file import process to send messages. Run the producer.
Does this meet the goal?
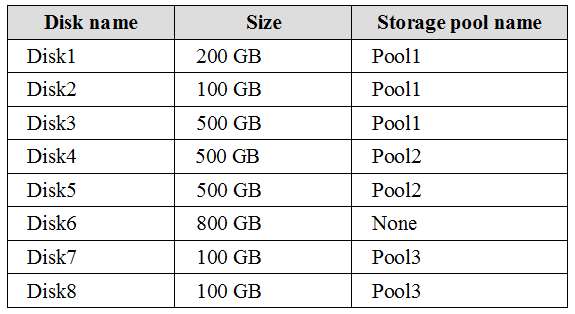
You need to remove Disk8 from Pool3
Note: This question is part of a series of questions that use the same set of answer choices. Each
answer choice may be used once, more than once, or not at all.
You have a computer named Computer1 that has storage configured as shown in the following table.
Pool3 contains a storage space named Space3 that is 100 GB.
Disk8 fails.
You add a new disk named Disk9 to Pool3.
You need to remove Disk8 from Pool3.
What should you use?
Only local users have permissions to Share
Note: This question is part of a series of questions that use the same scenario. For your convenience, the
scenario is repeated in each question. Each question presents a different goal and answer choices, but the text
of the scenario is exactly the same in each question in this series.
Your network contains a single Active Directory domain named adatum.com. The network contains five servers
configured as shown in the following table.
All of the servers run Windows Server 2012 R2.
Test_Server has a shared folder named ShareA. Only local users have permissions to ShareA.
The network contains a mainframe computer that is administered by using the Telnet protocol.
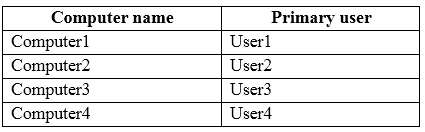
The domain contains four client computers configured as shown in the following table:
All of the client computers run the 64-bit version of Windows. User3 frequently accesses ShareA. Remote
Desktop is enabled on Computer4.
Your company identifies the following requirements:
Ensure that you can test unsigned device drivers on Computer1
Enable Credential Guard on Computer2.
Run commands and cmdlets remotely on Computer2.
Configure User Account Control (UAC) on Computer3 to prompt administrators for credentials when
elevated privileges are required.
Ensure that User1 can view and interact with a desktop session of User3.
Ensure that User2 can use Telnet to manage the mainframe.
Ensure that User4 can use Remote Desktop to access Computer4 remotely.
You need to meet the requirement of User4.
What should you do?
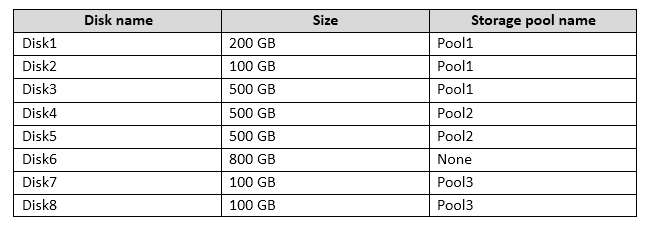
You need to configure Space3 to be 200 GB
Note: This question is part of a series of questions that use the same set of answer choices. Each answer
choice may be used once, more than once, or not at all.
You have a computer named Computer1 that has storage configured as shown in the following table.
Pool3 contains a storage space named Space3 that is 100 GB.
You need to configure Space3 to be 200 GB.
What should you use?
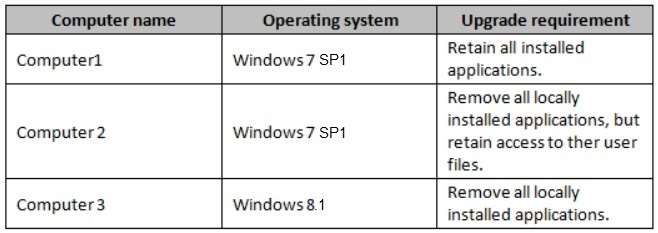
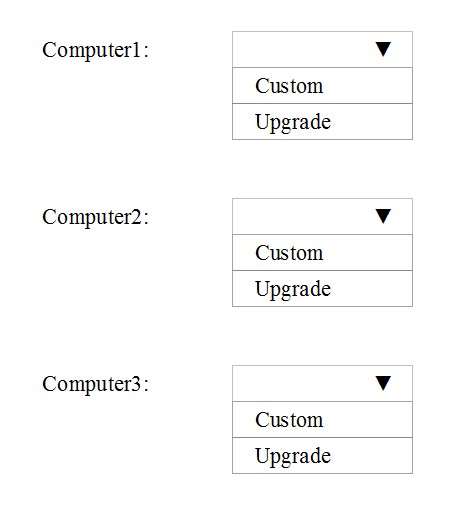
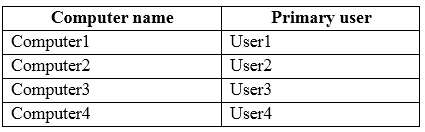
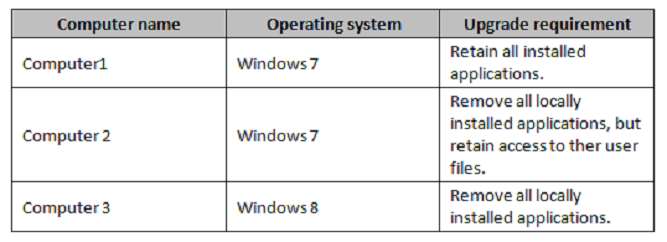
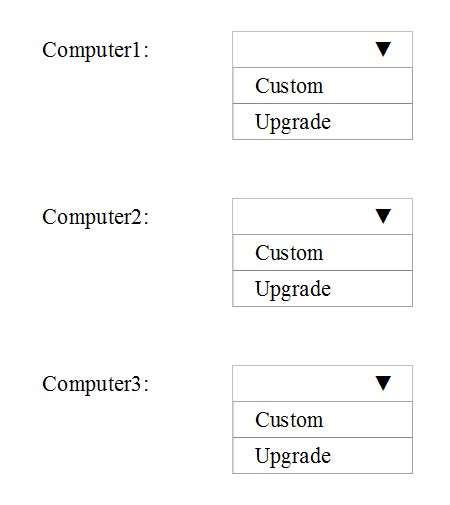
Which installation option should you use for each computer?
HOTSPOT
You have three computers configured as shown in the following table.
You plan to migrate the computers to Windows 10.
Which installation option should you use for each computer? To answer, select the appropriate options in the
answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Only local users have permissions to Share
Note: This question is part of a series of questions that use the same scenario. For your convenience, the
scenario is repeated in each question. Each question presents a different goal and answer choices, but the text
of the scenario is exactly the same in each question in this series.
Your network contains a single Active Directory domain named adatum.com.
The network contains five servers configured as shown in the following table:
All of the servers run Windows Server 2012 R2.
Test_Server has a shared folder named ShareA. Only local users have permissions to ShareA.
The network contains a mainframe computer that is administered by using the Telnet protocol.
The domain contains four client computers configured as shown in the following table:
All of the client computers run the 64-bit version of Windows 10. User3 frequently accesses ShareA. Remote
Desktop is enabled on Computer4.
Your company identifies the following requirements:
Ensure that you can test unsigned device drivers on Computer1.
Enable Credential Guard on Computer2.
Run commands and cmdlets remotely on Computer2.
Configure User Account Control (UAC) on Computer3to prompt administrators for credentials when
elevated privileges are required.
Ensure that User1 can view and interact with a desktop session of User3.
Ensure that User2 can use Telnet to manage the mainframe.
Ensure that User4 can use Remote Desktop to access Computer4 remotely.
You need to meet the Credential Guard requirement of Computer2.
Which Windows feature should you enable?