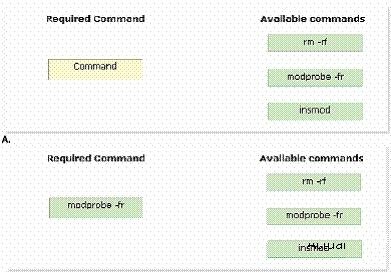
Which of the following commands will John use to accomplish his task?
What does this command do?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based
network. John is working as a root user on the Linux operating system. He has recently run the
yum clean packages command. What does this command do?
Which of the following statements is true about the sticky bit?
Which of the following statements is true about the sticky bit?
Which of the following commands will you use to accomplish the task?
You are a newly appointed network technician at Net Perfect Inc. The company has a Linux-based
network. You want to install a package named firefox on your Linux system. Which of the following
commands will you use to accomplish the task?
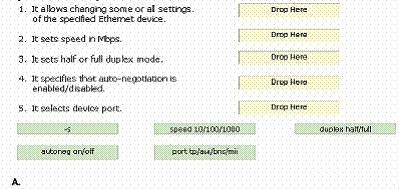
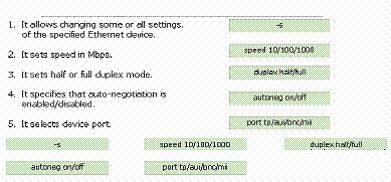
Drag and drop the appropriate option before its respective function.
Which of the following commands configures a new printer or changes the configuration of the existing printer?
Which of the following commands configures a new printer or changes the configuration of the
existing printer?
Which of the following commands will you use to accomplish the task?
You work as a System Administrator for McNeil Inc. The company has a Linux-based network.
You are a root user on the Red Hat operating system. You have added a new swap partition on
/dev/hdb2. After adding the new swap partition and enabling it, you want to ensure that it is
enabled. Which of the following commands will you use to accomplish the task?
Each correct answer represents a complete solution. Choose two.
_________is a network diagnostic tool that combines the functionality of the traceroute and ping programs in a
Fill in the blank with the appropriate tool.
_________is a network diagnostic tool that combines the functionality of the traceroute and ping
programs in a single network diagnostic tool.
Which of the following run-levels causes an X-based login to appear when the system is booted?
Which of the following run-levels causes an X-based login to appear when the system is booted?
which of the following statements are true?
John works as a professional Ethical Hacker. He has been assigned a project to test the security
of www.weare-secure.com. He enters the following command on the Linux terminal: chmod 741
secure.c Considering the above scenario, which of the following statements are true?
Each correct answer represents a complete solution. Choose all that apply.