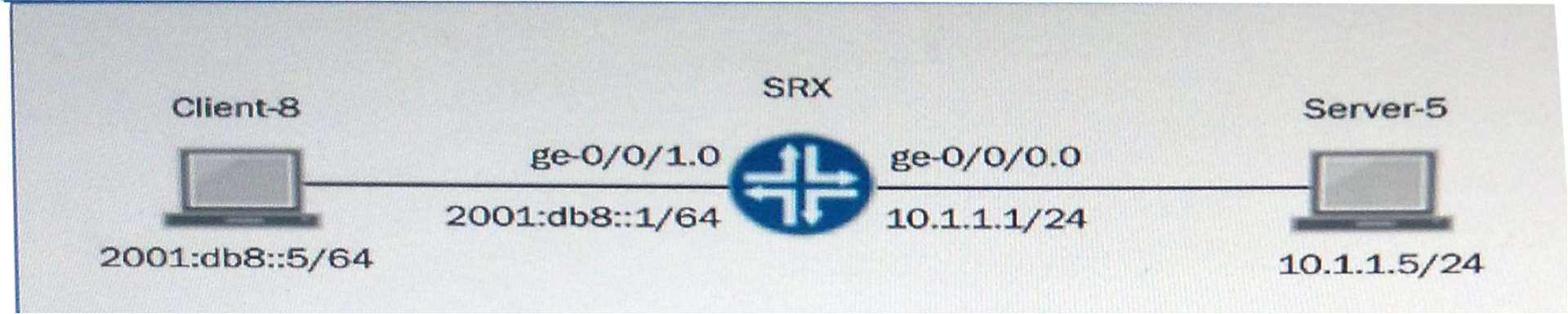
Which configurable SRX Series device feature allows you…
Which configurable SRX Series device feature allows you to capture transit traffic?
What are three techniques to mark DSCP values on an SRX…
What are three techniques to mark DSCP values on an SRX Series device? (Choose three.)
Which command set would allow the administrator to trou…
Click the Exhibit button.
root@host# show system login
user user {
uid 2000;
class operator;
authentication {
encrypted-password “$1$4s7ePrk5$9S.MZTwmXTV7sovJZFFsw1”; ## SECRET-DATA
]
}
An SRX Series device has been configured for multiple certificate-based VPNs. The IPsec security association
used for data replication is currently down . The administrator is a contractor and has the permissions on the
SPX Series device as shown in the exhibit
Which command set would allow the administrator to troubleshoot the cause for the VPN being down?
Which statement is correct?
You are asked to ensure that your IPS engine blocks attacks. You must ensure that your system continues to
drop additional malicious traffic without additional IPS processing for up to 30 minutes. You must ensure that
the SRX Series device does send a notification packet when the traffic is dropped.
Which statement is correct?
Which two configurations would resolve the problem?
Which statement is true regarding destination NAT?
Which statement is true regarding destination NAT?
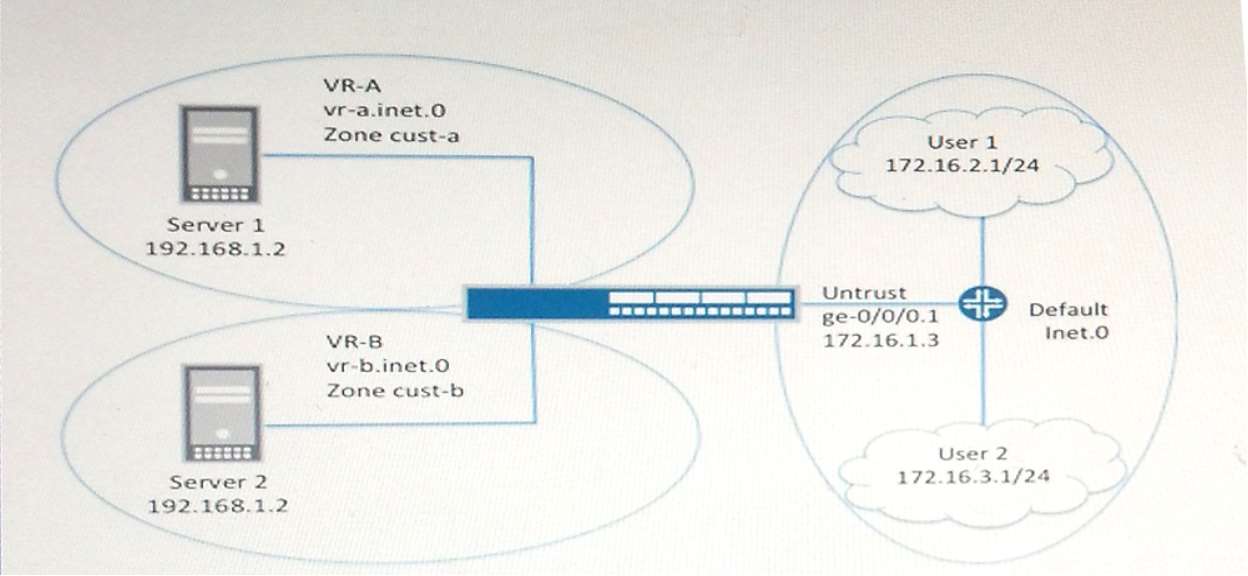
Which two methods of forwarding, between virtual router…
You want to route traffic between two newly created virtual routers without the use of logical systems using the
configuration options on the SRX5800.
Which two methods of forwarding, between virtual routers, would you recommend? (Choose two.)
You need to ensure that return traffic is able to reach…
Click the Exhibit button.
userehost# run show route
inet.0: 4 destinations, 4 routes (4 active, 0 holddown, 0 hidden)
+ = Active Route, – = Last Active, * = Both
0.0.0.0/0 *[Static/5] 00:05:06
> to 172.16.1.1 via ge-0/0/1.0
172.16.1.0/24 *[Direct/O] 00:05:06
> via ge-0/0/1.0
172.16.1.3/32 *[Local/0] 00:05:07
Local via ge-0/0/1.0
192.168.200.2/32 *[Local/0] 00:05:07
Rejectvr-a.inet.0: 2 destinations, 2 routes (2 active, 0 holddown, 0 hidden) + = Active Route, – = Last Active, * = Both
192.168.1.0/24 *[Direct/0] 00:01:05
> via ge-0/0/2.0
192.168.1.1/32 *[Local/0] 00:01:05
Local via ge-0/0/2.0
vr-b.inet.0: 2 destinations, 2 routes (2 active, 0 holddcwn, 0 hidden) + = Active Route, – = Last Active, * = Both
192.168.1.0/24 *[Direct/O] 00:01:05
> via go-0/0/3.0
192.168.1.1/32 *[Local/0] 00:01:05
Local via ge-0/0/3.0
User 1 will access Server 1 using IP address 10.2.1.1. You need to ensure that return traffic is able to reach
User 1 from Server 1.
Referring to the exhibit, which two configurations allow this communication (Choose two.)
which two statements are correct?
Click the Exhibit button.
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT:<1.1.1.100/51303->1.1.1.30/3389;6>
matched filter MatchTraffic:
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT:packet [48] ipid = 5015, @423d7e9e Feb 2 09:00:02
09:00:00.1872004:CID-0:RT:—- flow_process_pkt: (thd 1): flow_ctxt type 13, common flag Ox0, mbuf
Ox423d7d00
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: flow process pak fast ifl 72
In_ifp fe-0/0/7.0
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: fe-0/0/7.0:1.1.1.100/51303- >1.1.1.30/3389, top, flag 2 syn
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: find flow: table Ox5258d7b0, hash 17008(Oxffff), sa 1.1.1.100, da
1.1.1.30, sp 51303, dp 3389, proto 6, tok
448
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: no session found, start first
path. in_tunnel – 0, from_cp_flag – 0
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: flow_first_create_session
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: flow first_in_dst_nat: in <fe-0/0/7.0>, out <N/A> dst_adr 1.1.1.30,
sp 51303, dp 3389
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: chose interface fe-0/0/7.0 as incoming nat if.
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT:flow_first_rule_dst_xlate: packet 1.1.1.100->1.1.1.30 nsp2 0.0.0.0-
>192.168.224.30.
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT:flow_first_routing: call flow_route_lookup() src_ip 1.1.1.100,
x_dst_ip 192.168.224.30, in ifp fe-0/0/7.0, out ifp N/A sp 51303, dp 3389, ip_proto 6, tos 0
Feb 2 09:00:02 09:00:00.1872004:CID-O:RT:Doing DESTINATION addr route-lookup Feb 2 09:00:02
09:00:00.1872004:CID-0:RT: routed (x_dst_ip 192 168.224.30)
from untrust (fe-0/0/7.0 in 0) to ge-0/0/0.0, Next-hop: 192.168.224.30
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: policy search from zone untrust-> zone trust
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: policy has timeout 900
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: app 0, timeout 1800s, curr ageout 20s
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT:flow_first_src_xlate: src nat 0.0.0.0(51303) to 192.168.224.30
(3389) returns status 1, rule/pool id 1/2. Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: dip id = 2/0,
1.1.1.100/51303->192.168.224.3/48810
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: choose interface ge-0/0/0.0 as outgoing phy if
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT:is_loop_pak: No loop: on ifp: ge-0/0/0.0, addr: 192.168.224.30,
rtt_idx:0
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT:sm_flow_interest_check: app_id 0, policy 9, app_svc_en 0, flags
Ox2. not interested
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT:sm_flow_interest_check: app_id 1, policy 9, app_svc_en 0, flags
Ox2. not interested
Feb 2 09:00:02 09:00:00.1872004:CID-0:RT:flow_first_service_lookup(): natp(Ox51ee4680): app_id, 0(0).Feb 2 09:00:02 09:00:00.1872004:CID-0:RT: service lookup identified service O.
Referring to the exhibit, which two statements are correct? (Choose two.)
What is the cause of the problem?
Click the Exhibit button.
user@host> show security flow session extensive
Session ID: 1173, Status: Normal
Flag: Ox0
Policy name: two/6
Source NAT pool: interface, Application: junos-ftp/1
Dynamic application: junos:UNKNOWN,
Application traffic control rule-set: INVALID, Rule: INVALID
Maximum timeout: 1800, Current timeout: 1756
Session State: Valid
Start time: 4859, Duration: 99
In: 172.20.103.10/56457 –> 10.210.14.130/21;tcp,
Interface: vlan.103,
Session token: Ox8, Flag: Ox21
Route: 0x100010, Gateway: 172.20.103.10, Tunnel: 0
Port sequence: 0, FIN sequence: 0, FIN state: 0,
Pkts: 12, Bytes: 549
Out: 10.210.14.130/21 –> 10.210.14.133/18698;tcp,
Interface: ge-0/0/0.0,
Session token: 0x7, Flag: Ox20
Route: Oxf0010, Gateway: 10.210 14.130, Tunnel: 0
Port sequence: 0, FIN sequence: 0,
FIN state: 0,
Pkts: 8, Bytes: 514
Total sessions: 1A user complains that they are unable to download files using FTP. They are able to connect to the remote site,
but cannot download any files. You investigate and execute the show security flow session extensive command
to receive the result shown in the exhibit.
What is the cause of the problem?