which two services are allowed on the ge-0/0/2.0 interface?
Which additional configuration step is required?
— Exhibit —
[edit security policies from-zone untrust to-zone junos-host]
user@host# show
policy allow-management {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
[edit security zones security-zone untrust]
user@host# show
host-inbound-traffic {
protocols {
ospf;
}
}
interfaces {
ge-0/0/0.0;
}
— Exhibit —
Click the Exhibit button.
Referring to the exhibit, you want to be able to manage your SRX Series device from the
Internet using SSH. You have created a security policy to allow the traffic to flow into the
SRX device.
Which additional configuration step is required?
What is allowing hosts to access the Internet?
— Exhibit —
security {
policies {
from-zone TRUST to-zone UNTRUST {
policy hosts-allow {
match {
source-address hosts;
destination-address any;
application any;
}
then {
permit;
}
scheduler-name block-hosts;
}
policy allow {
match {
source-address any;
destination-address any;
application junos-http;
}
then {
permit;
}
}
policy deny {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
}
schedulers {
scheduler block-hosts {
daily {
start-time 10:00:00 stop-time 18:00:00;
}
}
}
— Exhibit —
Click the Exhibit button.
Referring to the exhibit, you have configured a scheduler to allow hosts access to the
Internet during specific times. You notice that hosts are still accessing the Internet during
times outside of the scheduler’s parameters.
What is allowing hosts to access the Internet?
The policy allow is allowing hosts access during unscheduled hours.
What is blocking hosts from accessing the Internet?
— Exhibit —
security {
policies {
from-zone TRUST to-zone UNTRUST {
policy allow-all {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
policy allow-hosts {
match {
source-address hosts;
destination-address any;
application junos-http;
}
then {
permit;
}
scheduler-name block-hosts;
}
policy deny {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
}
schedulers {
scheduler block-hosts {
daily {
start-time 10:00:00 stop-time 18:00:00;
}
}
}
— Exhibit —
Click the Exhibit button.
Referring to the exhibit, you have configured a scheduler to allow hosts access to the
Internet during specific times. You notice that hosts are unable to access the Internet.
What is blocking hosts from accessing the Internet?
which policy will allow traffic from Host 1, Host 2, and Host 3 to the Internet?
Which configuration will accomplish this task?
— Exhibit —
[edit security policies]
user@host# show
from-zone hr to-zone internet {
policy internet-access {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
policy clean-up {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
— Exhibit —
Click the Exhibit button.
You want to permit access to the Internet from the hr zone during a specified time.
Which configuration will accomplish this task?
Which additional step is required at the hub site for users to access the Web server?
Click the Exhibit button.
You are asked to configure a hub-and-spoke VPN. All the VPN components have been
configured, and you are able to ping the remote tunnel interfaces at Site 1 and Site 2 from
the Hub site as shown in the exhibit. The Hub site’s external interface is in security zone
untrust and the st0 interfaces from each site are in security zone DMZ. Users in Site 2 are
unable to connect to a Web server in Site 1.
Which additional step is required at the hub site for users to access the Web server?
you need to allow FTP traffic from the Internet to the FTP server in the Trust zone
Click the Exhibit button.
Referring to the exhibit, you need to allow FTP traffic from the Internet to the FTP server in
the Trust zone. You have built a custom application so that you can modify the timeout value
for FTP sessions and have configured a policy to allow FTP traffic from Untrust to Trust, but
the traffic still does not flow. The current status of the FTP ALG is disabled.
What is the problem?
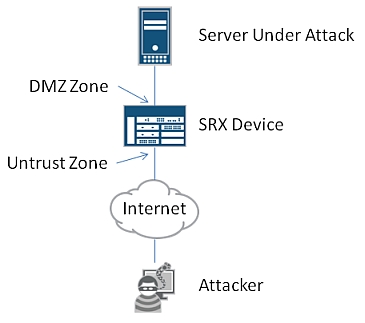
which Junos Screen option should you enable to limit the effects of the attack while allowing legitimate traff
Click the Exhibit button.
A server in the DMZ of your company is under attack. The attacker is opening a large
number of TCP connections to your server which causes resource utilization problems on
the server. All of the connections from the attacker appear to be coming from a single IP
address.
Referring to the exhibit, which Junos Screen option should you enable to limit the effects of
the attack while allowing legitimate traffic?