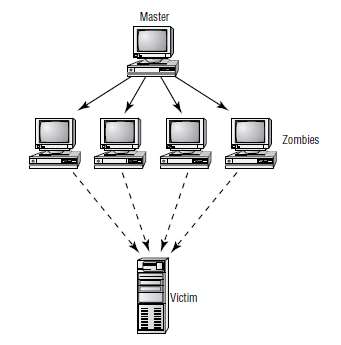
View the image below and identify the attack

A.
DDoS
B.
DoS
C.
TFN
D.
Reflection Attack
Explanation:
When a hacker has a collection of compromised systems, it is referred to as a botnet (network of bots). In the
exhibit they are marked as zombies. The hacker can use all of these systems to carry out powerful distributeddenial-of-service (DDoS) attacks or even rent these systems to spammers. The owner of this botnet controls
the systems remotely, usually through the Internet Relay Chat (IRC) protocol.
Incorrect Answers:
B: A DoS attack is similar to a DDoS attack, but in a DoS attack there is only one single source of the attack.
C: The Tribe Flood Network or TFN is a set of computer programs to conduct various DDoS attacks such as
ICMP flood, SYN flood, UDP flood and Smurf attack. From the exhibit we have no evidence of a TFN attack,
just of a DDoS attack.
D: A reflection attack is a method of attacking a challenge-response authentication system that uses the same
protocol in both directions. That is, the same challenge-response protocol is used by each side to authenticate
the other side. A reflection attack uses only a single computer as source, not a set of zombie computers.Harris, Shon, All In One CISSP Exam Guide, 6th Edition, McGraw-Hill, New York, 2013, p. 1204