Which of the following involves changing data prior to or during input to a computer in an effort to commit fr
Which of the following involves changing data prior to or during input to a computer in an effort to
commit fraud?
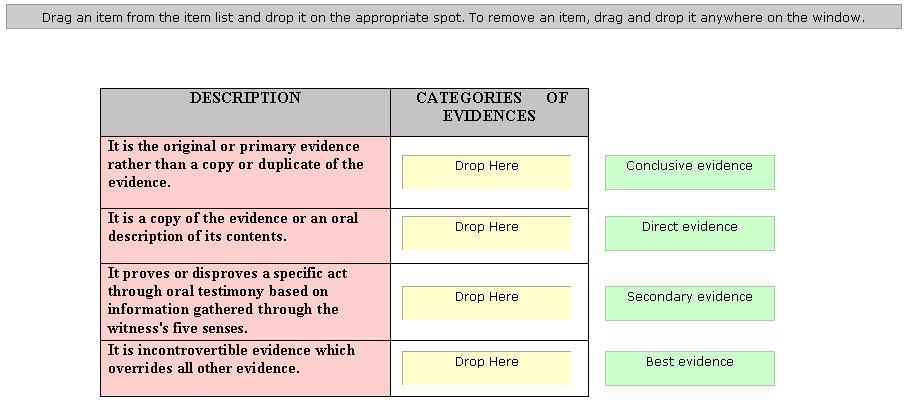
Drag and drop the various evidences in the appropriate places.
Which of the following penetration testing phases involves reconnaissance or data gathering?
Which of the following penetration testing phases involves reconnaissance or data gathering?
Which of the following protocols multicasts messages and information among all member devices in an IP multica
Which of the following protocols multicasts messages and information among all member devices in
an IP multicast group?
Which of the following penetration testing phases involves reconnaissance or data gathering?
Which of the following penetration testing phases involves reconnaissance or data gathering?
which Mark is involved?
Mark works as a security manager for SoftTech Inc. He is involved in the BIA phase to create a
document to be used to help understand what impact a disruptive event would have on the
business. The impact might be financial or operational. Which of the following are the objectives
related to the above phase in which Mark is involved?
Each correct answer represents a part of the solution. Choose three.
Which of the following security devices is presented to indicate some feat of service…?
Which of the following security devices is presented to indicate some feat of service, a special
accomplishment, a symbol of authority granted by taking an oath, a sign of legitimate employment
or student status, or as a simple means of identification?
Which of the following is a method for transforming a message into a masked form…?
Which of the following is a method for transforming a message into a masked form, together with a
way of undoing the transformation to recover the message?
Which of the following recovery plans includes specific strategies and actions to deal…?
Which of the following recovery plans includes specific strategies and actions to deal with specific
variances to assumptions resulting in a particular security problem, emergency, or state of affairs?
Which of the following protocols is used with a tunneling protocol to provide security?
Which of the following protocols is used with a tunneling protocol to provide security?