If an investigator needs to communicate with another investigator but does not want the criminal to be able to
If an investigator needs to communicate with another investigator but does not want the criminal to be able to eavesdrop on this conversation, what type of communication should be used?
Why is it challenging to collect and identify computer evidence to be used in a court of law?
Why is it challenging to collect and identify computer evidence to be used in a court of law?
Why is it difficult to investigate computer crime and track down the criminal?
Why is it difficult to investigate computer crime and track down the criminal?
Which of the following would be a violation of the (ISC)2 Code of Ethics that could cause the candidate to los
A CISSP candidate signs an ethics statement prior to taking the CISSP examination. Which of the following would be a violation of the (ISC)2 Code of Ethics that could cause the candidate to lose his or her certification?
After a computer forensics investigator seizes a computer during a crime investigation, what is the next step?
After a computer forensics investigator seizes a computer during a crime investigation, what is the next step?
Which of the following does the IAB consider unethical behavior?
Which of the following does the IAB consider unethical behavior?
Which of the following does the IAB consider unethical?
Which of the following does the IAB consider unethical?
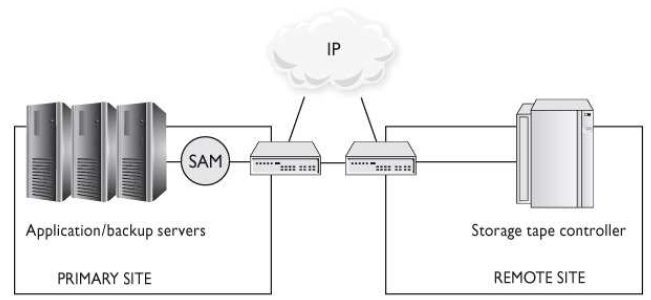
What type of technology is shown in the graphic that follows?
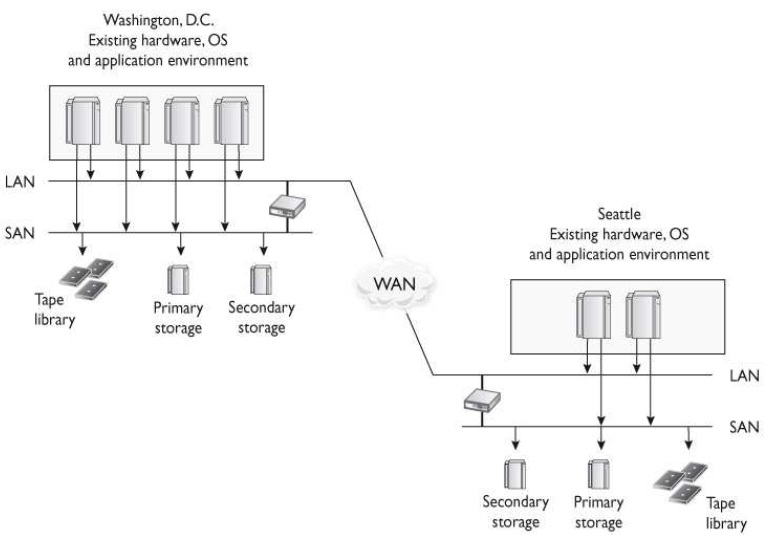
What type of infrastructural setup is illustrated in the graphic that follows?
Which ranking approach is illustrated in the graphic that follows?
Different threats need to be evaluated and ranked based upon their severity of business risk when developing a BCP. Which ranking approach is illustrated in the graphic that follows?
Choose the following statement that best describes the effect on this business unit/cost center should there be an unplanned interruption of normal business operations.
8 hours of an interruption. This business unit/cost center is Vital.
24 hours of an interruption. This business unit/cost center is Critical.
3 days of an interruption. This business unit/cost center is Essential.
5 days of an interruption. This business unit/cost center is Important.
10 days of an interruption. This business unit/cost center is Noncritical.
30 days of an interruption. This business unit/cost center is Deferrable.