How is a challenge/response protocol utilized with token device implementations?
How is a challenge/response protocol utilized with token device implementations?
An access control model should be applied in a…
An access control model should be applied in a _______________ manner.
Which access control policy is enforced when an environment uses a nondiscretionary model?
Which access control policy is enforced when an environment uses a nondiscretionary model?
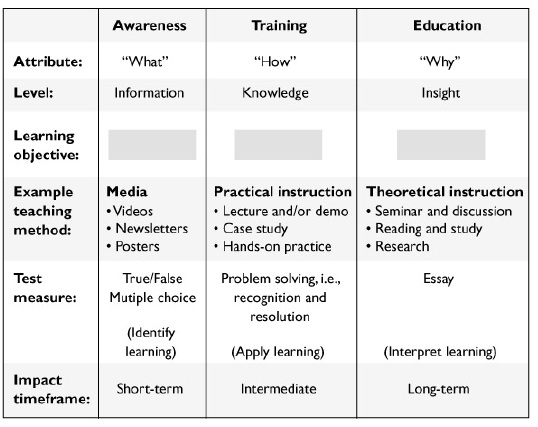
List in the proper order from the table on the top of the next page the learning objectives that are missing a
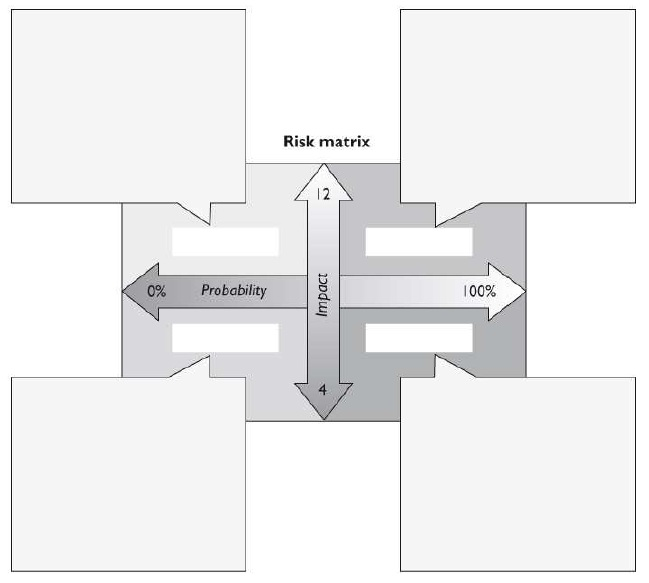
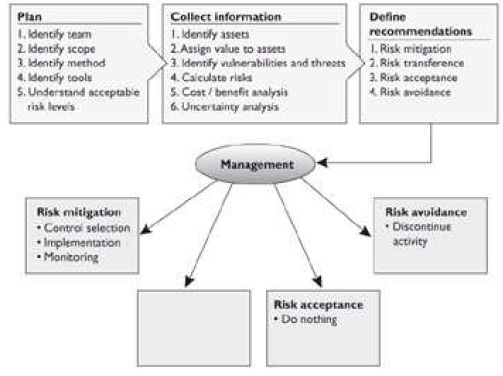
What type of risk analysis approach does the following graphic provide?
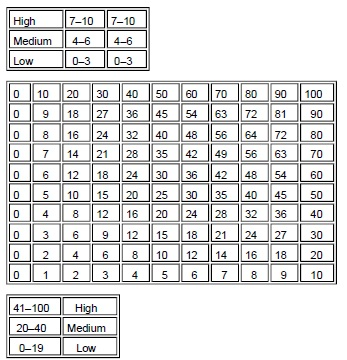
The following graphic contains a commonly used risk management scorecard. Identify the proper quadrant and its
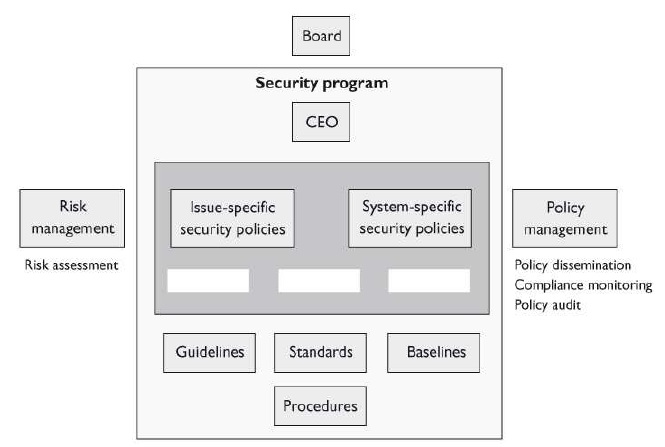
What are the three types of policies that are missing from the following graphic?
In the graphic that follows, which method is missing and what is the purpose of this method?
Which of the following should he do first?
Michael is charged with developing a classification program for his company. Which of the following should he do first?
Which of the following is not a characteristic of a company with a security governance program in place?
Which of the following is not a characteristic of a company with a security governance program in place?