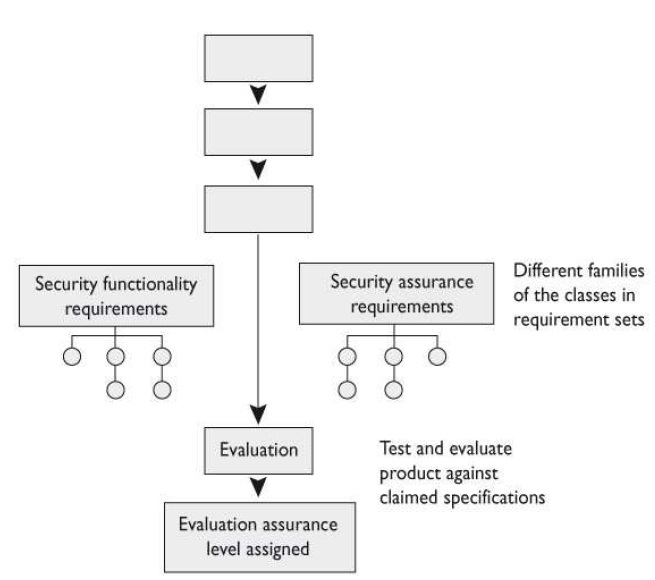
Which of the following best describes the first of the missing components?
Which of the following is considered the core set and focuses on the overall planning of the intended IT servi
The Information Technology Infrastructure Library (ITIL) consists of five sets of instructional books. Which of the following is considered the core set and focuses on the overall planning of the intended IT services?
Which of the following is used when the CPU sends data to an I/O device and then works on another process̵
There are different ways that operating systems can carry out software I/O procedures. Which of the following is used when the CPU sends data to an I/O device and then works on another process’s request until the I/O device is ready for more data?
Which of the following statements correctly describes the differences between two types of ROM?
Several types of read-only memory devices can be modified after they are manu`factured. Which of the following statements correctly describes the differences between two types of ROM?
Which of the following refers to a method in which an interface defines how communication can take place betwe
Operating systems can be programmed to carry out different methods for process isolation. Which of the following refers to a method in which an interface defines how communication can take place between two processes and no process can interact with the other’s internal programming code?
Which of the following is not a responsibility of the memory manager?
Which of the following is not a responsibility of the memory manager?
Which security architecture model defines how to securely develop access rights between subjects and objects?
Which security architecture model defines how to securely develop access rights between subjects and objects?
Which of the following incorrectly describes virtualization?
Virtualization offers many benefits. Which of the following incorrectly describes virtualization?
Which of the following refers to a concept that attempts to prevent this type of scenario from occurring?
Bethany is working on a mandatory access control (MAC) system. She has been working on a file that was classified as Secret. She can no longer access this file because it has been reclassified as Top Secret. She deduces that the project she was working on has just increased in confidentiality and she now knows more about this project than her clearance and need-to-know allows. Which of the following refers to a concept that attempts to prevent this type of scenario from occurring?
Which of the following best defines a virtual machine?
Which of the following best defines a virtual machine?