which of the following should be the PRIMARY concern regarding the database information?
Refer to the information below to answer the question.
During the investigation of a security incident, it is determined that an unauthorized individual
accessed a system which hosts a database containing financial information.
Aside from the potential records which may have been viewed, which of the following should be the
PRIMARY concern regarding the database information?
what attribute of the data has been compromised?
Refer to the information below to answer the question.
During the investigation of a security incident, it is determined that an unauthorized individual
accessed a system which hosts a database containing financial information.
If it is discovered that large quantities of information have been copied by the unauthorized
individual, what attribute of the data has been compromised?
which of the following has been affected?
Refer to the information below to answer the question.
During the investigation of a security incident, it is determined that an unauthorized individual
accessed a system which hosts a database containing financial information.
If the intrusion causes the system processes to hang, which of the following has been affected?
Which of the following will be the PRIMARY security concern as staff is released from the organization?
Refer to the information below to answer the question.
An organization experiencing a negative financial impact is forced to reduce budgets and the number
of Information Technology (IT) operations staff performing basic logical access security
administration functions. Security processes have been tightly integrated into normal IT operations
and are not separate and distinct roles.
Which of the following will be the PRIMARY security concern as staff is released from the
organization?
Which of the following will MOST likely allow the organization to keep risk at an acceptable level?
Refer to the information below to answer the question.
An organization experiencing a negative financial impact is forced to reduce budgets and the number
of Information Technology (IT) operations staff performing basic logical access security
administration functions. Security processes have been tightly integrated into normal IT operations
and are not separate and distinct roles.
Which of the following will MOST likely allow the organization to keep risk at an acceptable level?
Which of the following will indicate where the IT budget is BEST allocated during this time?
Refer to the information below to answer the question.
An organization experiencing a negative financial impact is forced to reduce budgets and the number
of Information Technology (IT) operations staff performing basic logical access security
administration functions. Security processes have been tightly integrated into normal IT operations
and are not separate and distinct roles.
Which of the following will indicate where the IT budget is BEST allocated during this time?
which of the following is MOST important to monitor?
Refer to the information below to answer the question.
An organization experiencing a negative financial impact is forced to reduce budgets and the number
of Information Technology (IT) operations staff performing basic logical access security
administration functions. Security processes have been tightly integrated into normal IT operations
and are not separate and distinct roles.
When determining appropriate resource allocation, which of the following is MOST important to
monitor?
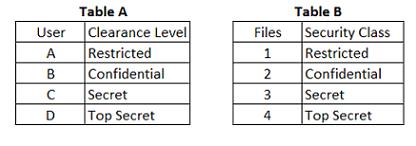
Which of the following is true according to the star property (*property)?
Refer to the information below to answer the question.
In a Multilevel Security (MLS) system, the following sensitivity labels are used in increasing levels of
sensitivity: restricted, confidential, secret, top secret. Table A lists the clearance levels for four users,
while Table B lists the security classes of four different files.
Which of the following is true according to the star property (*property)?
which user cannot write to File 3?
Refer to the information below to answer the question.In a Multilevel Security (MLS) system, the following sensitivity labels are used in increasing levels of
sensitivity: restricted, confidential, secret, top secret. Table A lists the clearance levels for four users,
while Table B lists the security classes of four different files.
In a Bell-LaPadula system, which user cannot write to File 3?
which user has the MOST restrictions when writing data to any of the four files?
Refer to the information below to answer the question.
In a Multilevel Security (MLS) system, the following sensitivity labels are used in increasing levels of
sensitivity: restricted, confidential, secret, top secret. Table A lists the clearance levels for four users,
while Table B lists the security classes of four different files.
In a Bell-LaPadula system, which user has the MOST restrictions when writing data to any of the four
files?