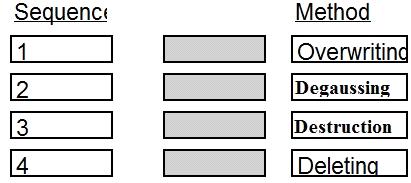
Place in order, from BEST (1) to WORST (4), the following methods to reduce the risk…
Which of the following methods can be used to achieve confidentiality and integrity for data in transit?
Which of the following methods can be used to achieve confidentiality and integrity for data in
transit?
Secure Sockets Layer (SSL) encryption protects
Secure Sockets Layer (SSL) encryption protects
Which of the following are Systems Engineering Life Cycle (SELC) Technical Processes?
Which of the following are Systems Engineering Life Cycle (SELC) Technical Processes?
Which of the following BEST describes a Protection Profile (PP)?
Which of the following BEST describes a Protection Profile (PP)?
Which of the following BEST describes a rogue Access Point (AP)?
Which of the following BEST describes a rogue Access Point (AP)?
which of the following?
Single Sign-On (SSO) is PRIMARILY designed to address which of the following?
The 802.1x standard provides a framework for what?
The 802.1x standard provides a framework for what?
Which of the following is the PRIMARY security concern associated with the implementation of smart cards?
Which of the following is the PRIMARY security concern associated with the implementation of
smart cards?
Which of the following is a function of Security Assertion Markup Language (SAML)?
Which of the following is a function of Security Assertion Markup Language (SAML)?