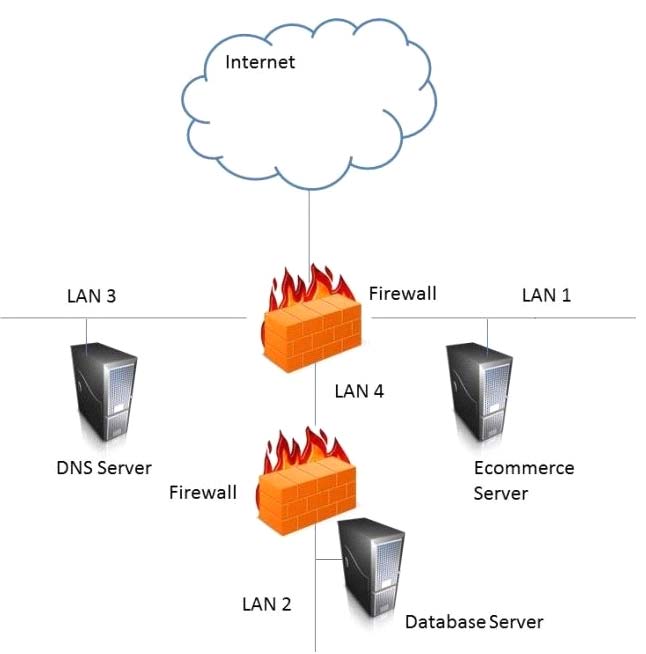
where is the MOST secure Local Area Network (LAN) segment to deploy a Wireless Access Point…?
Which of the following is the PRIMARY concern when using an Internet browser to access a cloudbased service?
Which of the following is the PRIMARY concern when using an Internet browser to access a cloudbased service?
Which of the following BEST mitigates this issue?
After a thorough analysis, it was discovered that a perpetrator compromised a network by gaining
access to the network through a Secure Socket Layer (SSL) Virtual Private Network (VPN) gateway.
The perpetrator guessed a username and brute forced the password to gain access. Which of the
following BEST mitigates this issue?
which of the following is MOST secure?
For an organization considering two-factor authentication for secure network access, which of the
following is MOST secure?
what is the interpretation of this result?
If an identification process using a biometric system detects a 100% match between a presented
template and a stored template, what is the interpretation of this result?
which of the following INITIAL top three areas are important to focus on?
Regarding asset security and appropriate retention, which of the following INITIAL top three areas
are important to focus on?
which of the following?
Discretionary Access Control (DAC) is based on which of the following?
which of the following defines the opening of a mechanical lock without the proper key?
By carefully aligning the pins in the lock, which of the following defines the opening of a mechanical
lock without the proper key?
which of the following must the end user provide?
An organization has decided to contract with a cloud-based service provider to leverage their
identity as a service offering. They will use Open Authentication (OAuth) 2.0 to authenticate external
users to the organization’s services.
As part of the authentication process, which of the following must the end user provide?
What would be the MOST probable cause?
An organization is found lacking the ability to properly establish performance indicators for its Web
hosting solution during an audit. What would be the MOST probable cause?