what is the MOST LIKELY security issue with degaussing?
Refer to the information below to answer the question.
Desktop computers in an organization were sanitized for re-use in an equivalent security
environment. The data was destroyed in accordance with organizational policy and all marking and
other external indications of the sensitivity of the data that was formerly stored on the magnetic
drives were removed.
After magnetic drives were degaussed twice according to the product manufacturer’s directions,
what is the MOST LIKELY security issue with degaussing?
Which destruction method below provides the BEST assurance that the data has been removed?
Refer to the information below to answer the question.
Desktop computers in an organization were sanitized for re-use in an equivalent security
environment. The data was destroyed in accordance with organizational policy and all marking and
other external indications of the sensitivity of the data that was formerly stored on the magnetic
drives were removed.
Organizational policy requires the deletion of user data from Personal Digital Assistant (PDA) devices
before disposal. It may not be possible to delete the user data if the device is malfunctioning. Which
destruction method below provides the BEST assurance that the data has been removed?
The third party needs to have
Refer to the information below to answer the question.
A large, multinational organization has decided to outsource a portion of their Information
Technology (IT) organization to a third-party provider’s facility. This provider will be responsible for
the design, development, testing, and support of several critical, customer-based applications used
by the organization.
The third party needs to have
The organization should ensure that the third party’s physical security controls are in place so that th
Refer to the information below to answer the question.
A large, multinational organization has decided to outsource a portion of their Information
Technology (IT) organization to a third-party provider’s facility. This provider will be responsible for
the design, development, testing, and support of several critical, customer-based applications used
by the organization.
The organization should ensure that the third party’s physical security controls are in place so that
they
What additional considerations are there if the third party is located in a different country?
Refer to the information below to answer the question.
A large, multinational organization has decided to outsource a portion of their Information
Technology (IT) organization to a third-party provider’s facility. This provider will be responsible for
the design, development, testing, and support of several critical, customer-based applications used
by the organization.
What additional considerations are there if the third party is located in a different country?
What is the MOST critical factor to achieve the goals of a security program?
What is the MOST critical factor to achieve the goals of a security program?
What components are in the scope of PCI-DSS?
A business has implemented Payment Card Industry Data Security Standard (PCI-DSS) compliant
handheld credit card processing on their Wireless Local Area Network (WLAN) topology.
The network team partitioned the WLAN to create a private segment for credit card processing using
a firewall to control device access and route traffic to the card processor on the Internet. What
components are in the scope of PCI-DSS?
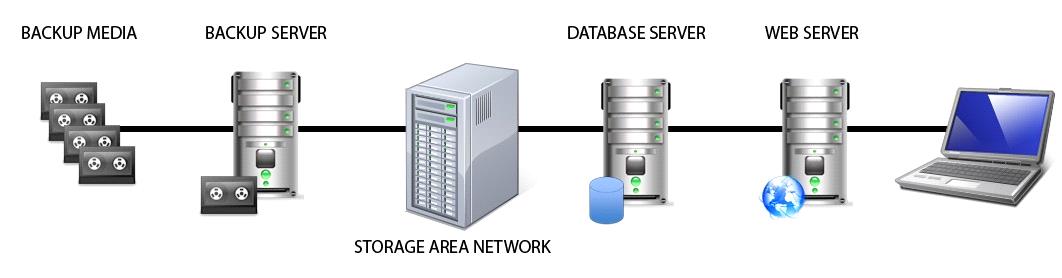
Identify the component that MOST likely lacks digital accountability related to information access.
Which of the following is the MOST appropriate action to take?
During an audit, the auditor finds evidence of potentially illegal activity. Which of the following is the
MOST appropriate action to take?