Which of the following types of cyber stalking damage the reputation of their victim…?
Which of the following types of cyber stalking damage the reputation of their victim and turn other
people against them by setting up their own Websites, blogs or user pages for this purpose?
Which of the following processes is a structured approach to transitioning individuals, teams, and organizatio
Which of the following processes is a structured approach to transitioning individuals, teams, and
organizations from a current state to a desired future state?
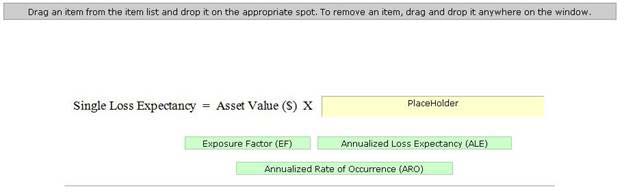
What will be the Single Loss Expectancy of the project?
Mark is the project manager of the NHQ project in Spartech Inc. The project has an asset valued at
$195,000 and is subjected to an exposure factor of 35 percent. What will be the Single Loss
Expectancy of the project?
Which of the following is the default port for Secure Shell (SSH)?
Which of the following is the default port for Secure Shell (SSH)?
Drop the appropriate value to complete the formula.
Which of the following is used to back up forensic evidences or data folders from the network or locally attac
Which of the following is used to back up forensic evidences or data folders from the network or
locally attached hard disk drives?
Which of the following steps are performed by you for secure recovery based on the extent of the disaster and
You work as a security manager for SoftTech Inc. You along with your team are doing the disaster
recovery for your project. Which of the following steps are performed by you for secure recovery
based on the extent of the disaster and the organization’s recovery ability?
Each correct answer represents a part of the solution. Choose three.
What phases are identified by DIACAP?
DIACAP applies to the acquisition, operation, and sustainment of any DoD system that collects,
stores, transmits, or processes unclassified or classified information since December 1997. What
phases are identified by DIACAP?
Each correct answer represents a complete solution. Choose all that apply.
What do you tell Bonny?
Management has asked you to perform a risk audit and report back on the results. Bonny, a project
team member asks you what a risk audit is. What do you tell Bonny?
Which of the following steps are generally followed in computer forensic examinations?
Which of the following steps are generally followed in computer forensic examinations?
Each correct answer represents a complete solution. Choose three.