Which of the following is most appropriate for this client?
You
are advising a school district on disaster recovery plans. In case a disaster affects the main IT centers
for the district they will need to be able to work from an alternate location. However, budget is an
issue. Which of the following is most appropriate for this client?
Which of the following BCP teams provides clerical support to the other teams and serves as a message center f
Which of the following BCP teams provides clerical support to the other teams and serves as a
message center for the user-recovery site?
Which of the following BCP teams provides clerical support to the other teams and serves as a message center f
Which of the following BCP teams provides clerical support to the other teams and serves as a
message center for the user-recovery site?
Which of the following are the centralized administration technologies?
Which
of the following are the centralized administration technologies? Each correct answer represents a
complete solution. Choose all that apply.
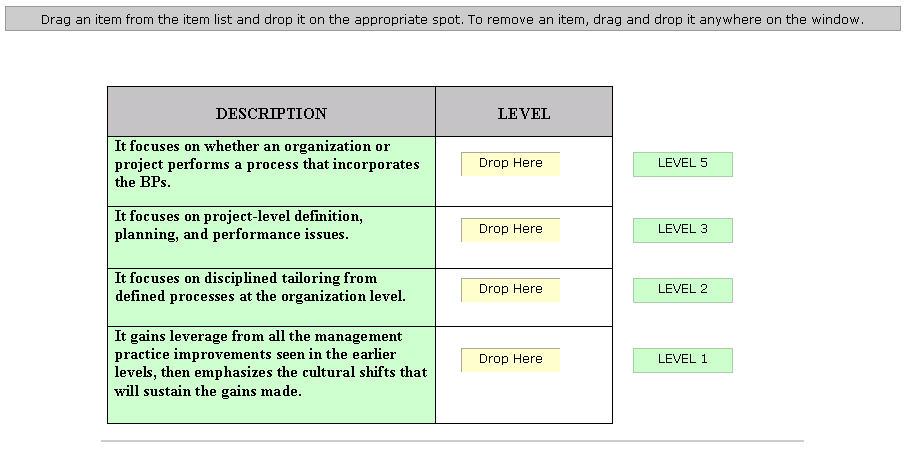
Drag and drop the various SSE-CMM levels at the appropriate places.
which was installed to permit system maintenance and to bypass the system’s security protections?
Which of the following architecturally related vulnerabilities is a hardware or software mechanism,
which was installed to permit system maintenance and to bypass the system’s security protections?
Which of the following steps will you perform to accomplish the task?
You have created a team of HR Managers and Project Managers for Blue Well Inc. The team will
concentrate on hiring some new employees for the company and improving the organization’s
overall security by turning employees among numerous job positions. Which of the following steps
will you perform to accomplish the task?
What is the likely outcome of creating this type of chart?
Your project has several risks that may cause serious financial impact should they happen. You have
studied the risk events and made some potential risk responses for the risk events but management
wants you to do more. They’d like for you to create some type of a chart that identified the risk
probability and impact with a financial amount for each risk event. What is the likely outcome of
creating this type of chart?
Which of the following persons is responsible for testing and verifying whether the security policy is properl
Which of the following persons is responsible for testing and verifying whether the security policy is
properly implemented, and the derived security solutions are adequate or not?
Which of the following are the process steps of OPSEC?
Which of the following are the process steps of OPSEC?
Each correct answer represents a part of the solution. Choose all that apply.