Which of the following should you use?
You have been assigned the task of selecting a hash algorithm. The algorithm will be specifically
used to ensure the integrity of certain sensitive files. It must use a 128 bit hash value. Which of the
following should you use?
Which of the following is most appropriate for this client?
You are advising a school district on disaster recovery plans. In case a disaster affects the main IT
centers for the district they will need to be able to work from an alternate location. However, budget
is an issue. Which of the following is most appropriate for this client?
Which of the following are the countermeasures against a man-in-the-middle attack?
Which of the following are the countermeasures against a man-in-the-middle attack? Each correct
answer represents a complete solution. Choose all that apply.
Which of the following is a process of monitoring data packets that travel across a network?
Which of the following is a process of monitoring data packets that travel across a network?
Which of the following is an electrical event shows that there is enough power on…?
Which of the following is an electrical event shows that there is enough power on the grid to
prevent from a total power loss but there is no enough power to meet the current electrical
demand?
Which of the following is a process of monitoring data packets that travel across a network?
Which of the following is a process of monitoring data packets that travel across a network?
Which of the following protocols is designed to efficiently handle high-speed data over wide area networks (WA
Which of the following protocols is designed to efficiently handle high-speed data over wide area
networks (WANs)?
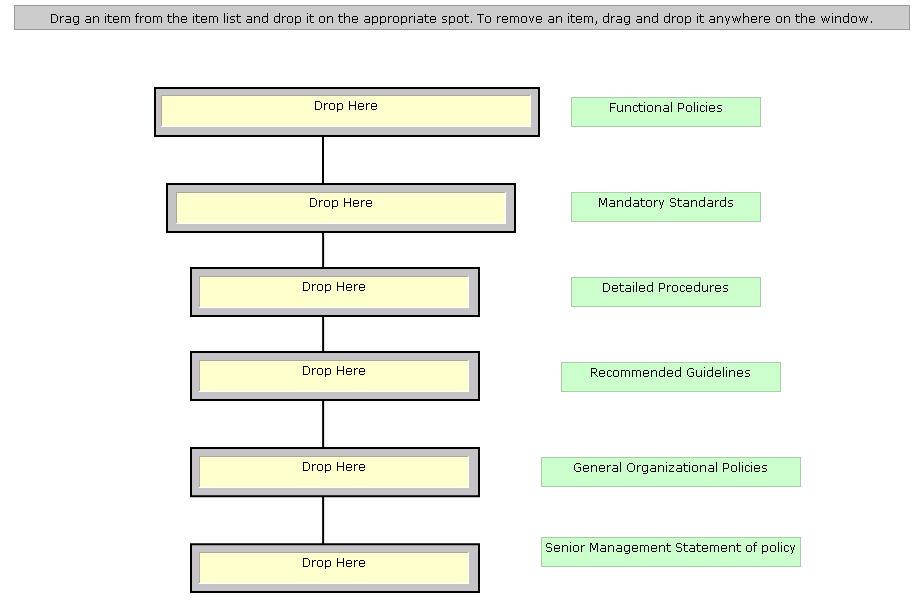
Drag and drop each policy statement according to its hierarchy level.
which of the following types of office sites is he working?
Mark works as a security manager for SofTech Inc. He is working in a partially equipped office space
which contains some of the system hardware, software, telecommunications, and power sources. In
which of the following types of office sites is he working?
Which of the following statements best describes a certification authority?
Which of the following statements best describes a certification authority?