Which of the following standards/guidelines requires an Information Security Management System (ISMS) to be de
Which of the following standards/guidelines requires an Information Security Management System
(ISMS) to be defined?
Which of the following PRIMARILY contributes to security incidents in web-based applications?
Which of the following PRIMARILY contributes to security incidents in web-based applications?
which order, from MOST to LEAST impacted, does user awareness training reduce the occurrence…?
What is the process called when impact values are assigned to the security objectives for information types?
What is the process called when impact values are assigned to the security objectives for
information types?
which of the following?
Data remanence refers to which of the following?
Which of the following describes the BEST configuration management practice?
Which of the following describes the BEST configuration management practice?
How does Encapsulating Security Payload (ESP) in transport mode affect the Internet Protocol (IP)?
How does Encapsulating Security Payload (ESP) in transport mode affect the Internet Protocol (IP)?
Which of the following is the MOST likely cause of a non-malicious data breach when the source of the data bre
Which of the following is the MOST likely cause of a non-malicious data breach when the source of
the data breach was an un-marked file cabinet containing sensitive documents?
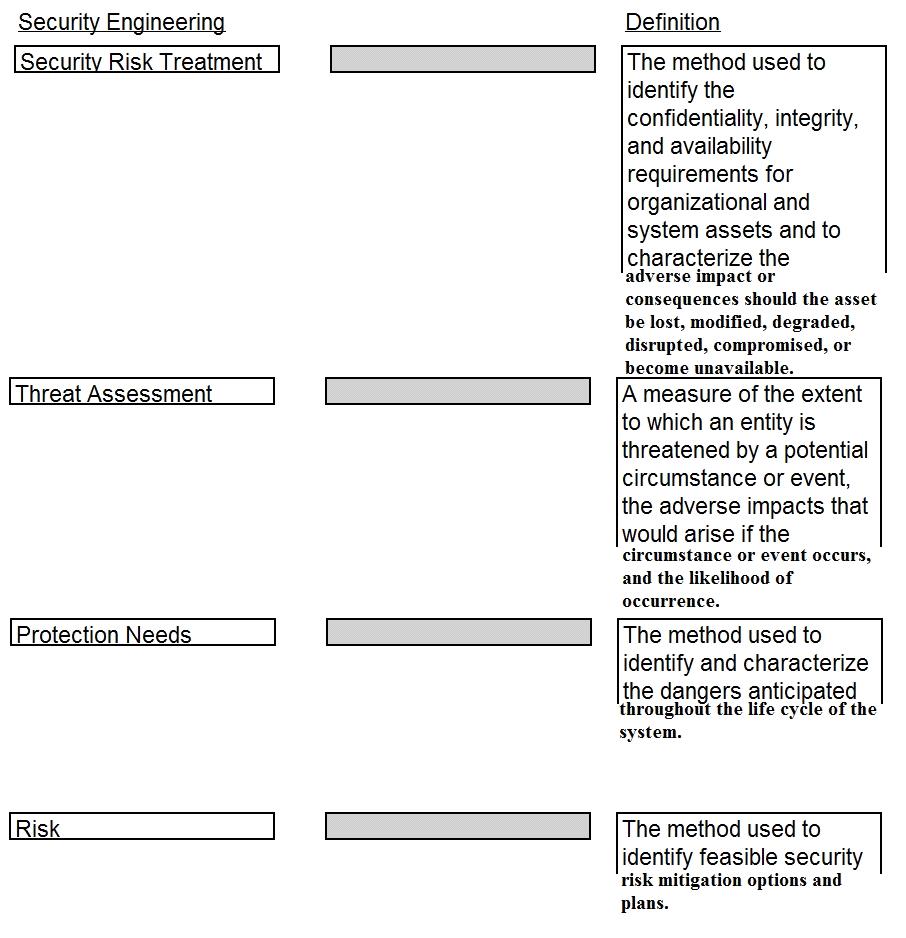
Drag the following Security Engineering terms on the left to the BEST definition on the right.
Which of the following is the BEST location?
A security professional has been asked to evaluate the options for the location of a new data center
within a multifloor building. Concerns for the data center include emanations and physical access
controls.
Which of the following is the BEST location?