The most insidious part of Phishing and Spear Phishing attacks comes from which part of the attack anatomy?
The most insidious part of Phishing and Spear Phishing attacks comes from which part of the attack anatomy?
What is the difference between password cracking and password guessing?
What is the difference between password cracking and password guessing?
What type of password cracking attack will always be successful?
What type of password cracking attack will always be successful?
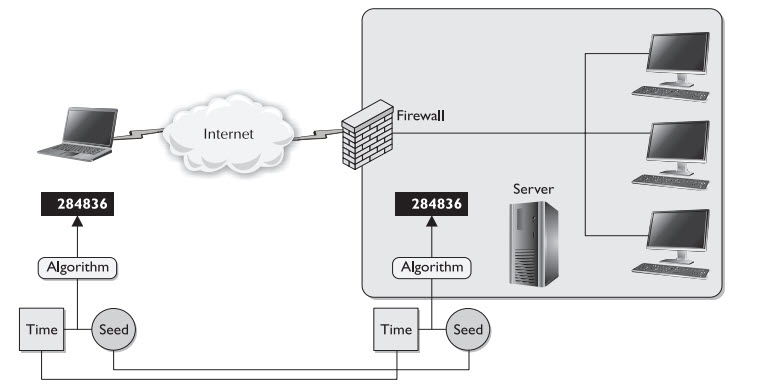
The graphic shown here illustrates how which of the following works…
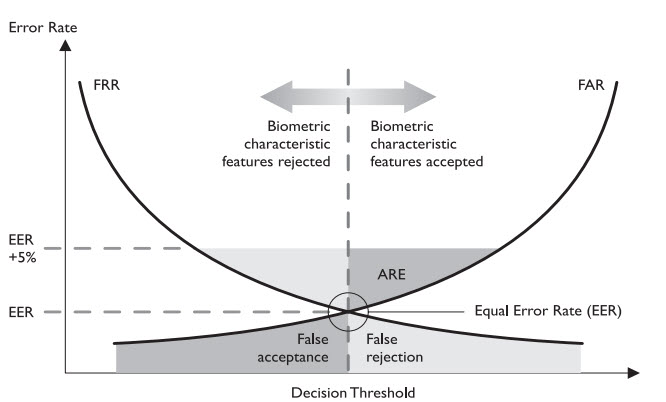
The diagram shown next explains which of the following concepts…
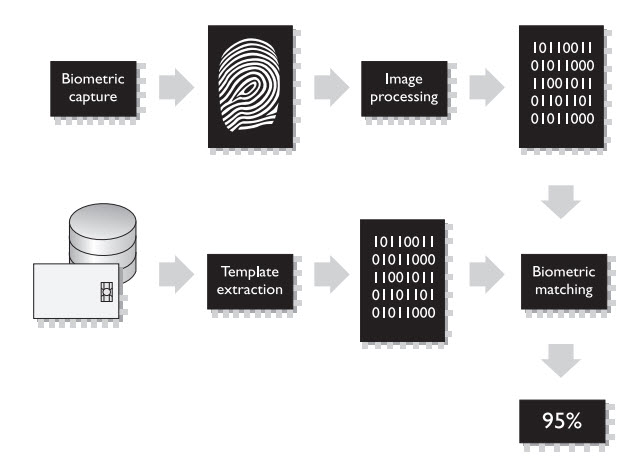
The next graphic covers which of the following…
Which of the following is not considered an anomaly-based intrusion protection system?
Which of the following is not considered an anomaly-based intrusion protection system?
What is the technology that allows a user to remember just one password?
What is the technology that allows a user to remember just one password?
Which of the following is not part of user provisioning?
Which of the following is not part of user provisioning?
Which of the following is the best description of directories and how they relate to identity management?
Which of the following is the best description of directories and how they relate to identity management?