How many bits is the address space reserved for the sou…
How many bits is the address space reserved for the source IP address within an IPv6 header?
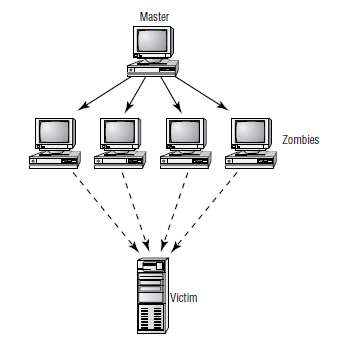
View the image below and identify the attack
The spoofed IP address used by the attacker as the sour…
What sort of attack is described by the following: An attacker has a list of broadcast addresses which it stores
into an array, the attacker sends a spoofed icmp echo request to each of those addresses in series and starts
again. The spoofed IP address used by the attacker as the source of the packets is the target/victim IP
address.
What protocol was used here to conduct the file transfer?
You are using an open source packet analyzer called Wireshark and are sifting through the various
conversations to see if anything appears to be out of order.
You are observing a UDP conversation between a host and a router. It was a file transfer between the two on
port 69. What protocol was used here to conduct the file transfer?
What is the three-way handshake sequence used to initia…
What is the three-way handshake sequence used to initiate TCP connections?
Which type of attack involves the altering of a systems…
Which type of attack involves the altering of a systems Address Resolution Protocol (ARP) table so that it
contains incorrect IP to MAC address mappings?
which multiple access method for computer networks does…
Of the following, which multiple access method for computer networks does 802.11 Wireless Local Area
Network use?
What is called an attack in which an attacker floods a …
What is called an attack in which an attacker floods a system with connection requests but does not respond
when the target system replies to those requests?
What is the BEST answer pertaining to the difference be…
What is the BEST answer pertaining to the difference between the Session and Transport layers of the OSI
model?
which OSI layer does SSL reside in?
At which OSI layer does SSL reside in?