What is the most cost effective method to prevent this?
You are the Network Administrator for a college. You watch a large number of people (some not
even students) going in and out of areas with campus computers (libraries, computer labs, etc.). You
have had a problem with laptops being stolen. What is the most cost effective method to prevent
this?
Which of the following is violated in a shoulder surfing attack?
Shoulder surfing is a type of in-person attack in which the attacker gathers information about the
premises of an organization. This attack is often performed by looking surreptitiously at the
keyboard of an employee’s computer while he is typing in his password at any access point such as a
terminal/Web site. Which of the following is violated in a shoulder surfing attack?
Which of the following plans provides procedures for recovering business operations immediately following a di
Which of the following plans provides procedures for recovering business operations immediately
following a disaster?
which is calculated as a percentage of the initial estimated project costs?
In which of the following contract types, the seller is reimbursed for all allowable costs for
performing the contract work and receives a fixed fee payment which is calculated as a percentage
of the initial estimated project costs?
Which of the following processes is a structured approach to transitioning individuals, teams, and organizatio
Which of the following processes is a structured approach to transitioning individuals, teams, and
organizations from a current state to a desired future state?
Which of the following types of cyber stalking damage the reputation of their victim…?
Which of the following types of cyber stalking damage the reputation of their victim and turn other
people against them by setting up their own Websites, blogs or user pages for this purpose?
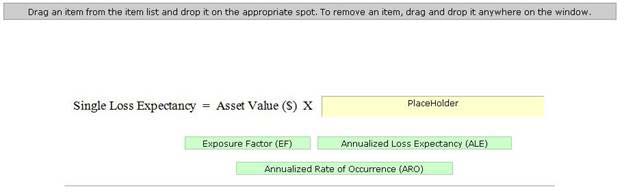
What will be the Single Loss Expectancy of the project?
Mark is the project manager of the NHQ project in Spartech Inc. The project has an asset valued at
$195,000 and is subjected to an exposure factor of 35 percent. What will be the Single Loss
Expectancy of the project?
Which of the following is the default port for Secure Shell (SSH)?
Which of the following is the default port for Secure Shell (SSH)?
Which of the following is used to back up forensic evidences or data folders from the network or locally attac
Which of the following is used to back up forensic evidences or data folders from the network or
locally attached hard disk drives?