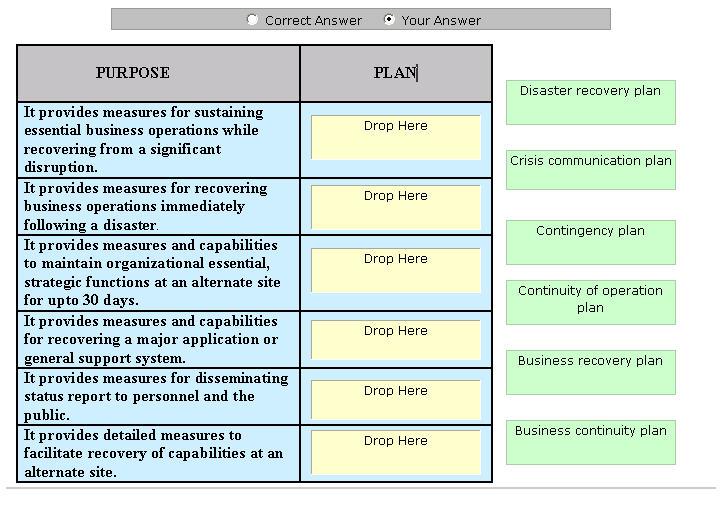
Which of the following representatives of incident response team takes forensic backups of the systems that ar
Which of the following representatives of incident response team takes forensic backups of the
systems that are the focus of the incident?
which of the following SDLC phases are the software and other components of the system faithfully incorporated
In which of the following SDLC phases are the software and other components of the system faithfully
incorporated into the design specifications?
Which of the following Internet laws has the credit card issuing company violated?
A Web-based credit card company had collected financial and personal details of Mark before
issuing him a credit card. The company has now provided Mark’s financial and personal details to
another company. Which of the following Internet laws has the credit card issuing company
violated?
Which of the following Internet laws has the credit card issuing company violated?
A Web-based credit card company had collected financial and personal details of Mark before
issuing him a credit card. The company has now provided Mark’s financial and personal details to
another company. Which of the following Internet laws has the credit card issuing company
violated?
Which of the following life cycle modeling activities establishes service relationships and message exchange p
Which
of the following life cycle modeling activities establishes service relationships and message exchange
paths?
Arrange the components according to their respective OSI layers.
How will you configure the Web server so that it is secure and only authenticated users are able to access it?
You work as a Web Administrator for Perfect World Inc. The company is planning to host an Ecommerce Web site. You are required to design a security plan for it. Client computers with different
operating systems will access the Web server. How will you configure the Web server so that it is
secure and only authenticated users are able to access it?
Each correct answer represents a part of the solution. Choose two.
Which of the following authentication methods support mutual authentication?
Which
of the following authentication methods support mutual authentication? Each correct answer
represents a complete solution. Choose two.
Which of the following statements are true about security risks?
Which of the following statements are true about security risks?
Each correct answer represents a complete solution. Choose three.
Which of the following keys is derived from a preshared key and Extensible Authentication Protocol (EAP)?
Which
of the following keys is derived from a preshared key and Extensible Authentication Protocol (EAP)?