you need to conduct to resolve the problem?
You work as a Network Administrator for ABC Inc. The company uses a secure wireless network.
John complains to you that his computer is not working properly. What type of security audit do you
need to conduct to resolve the problem?
which proves that the sender really sent a particular message?
Which of the following terms refers to a mechanism which proves that the sender really sent a
particular message?
Which of the following laws is the first to implement penalties for the creator of viruses, worms, and other t
Which of the following laws is the first to implement penalties for the creator of viruses, worms, and
other types of malicious code that causes harm to the computer systems?
Which of the following types of hardware devices will Adam use to implement two-factor authentication?
Adam works as a Security Analyst for Umbrella Inc. CEO of the company ordered him to implement
two-factor authentication for the employees to access their networks. He has told him that he would
like to use some type of hardware device in tandem with a security or identifying pin number. Adam
decides to implement smart cards but they are not cost effective. Which of the following types of
hardware devices will Adam use to implement two-factor authentication?
Fill in the blank with an appropriate phrase.________ models address specifications, requirements, and design,
Fill in the blank with an appropriate phrase.________ models address specifications, requirements,
and design, verification and validation, and maintenance activities.
Which of the following techniques will she use to fulfill this requirement?
Maria works as a Network Security Officer for Gentech Inc. She wants to encrypt her network traffic.
The specific requirement for the encryption algorithm is that it must be a symmetric key block
cipher. Which of the following techniques will she use to fulfill this requirement?
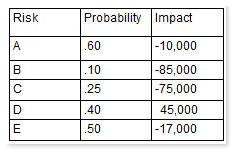
How much capital should the project set aside for the risk contingency reserve?
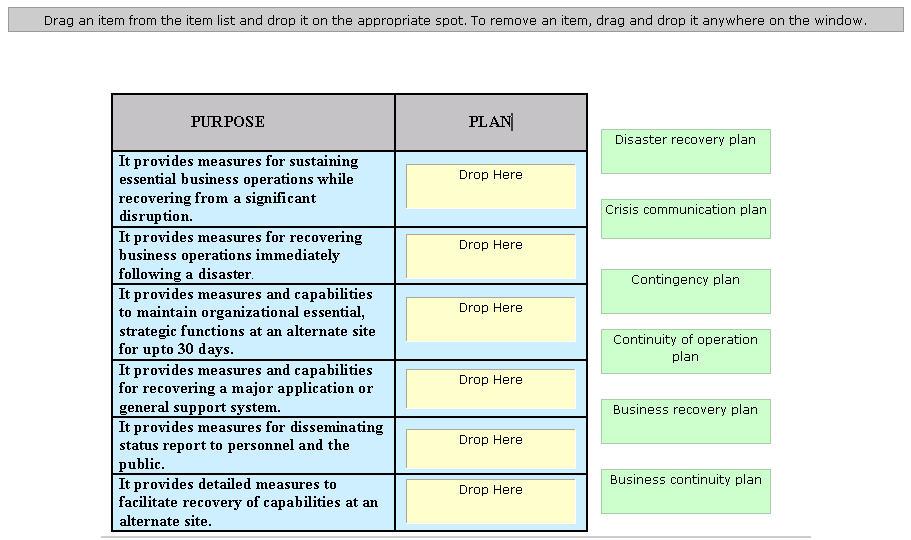
Drag and drop the Response management plans to match up with their respective purposes.
Which of the following protocols uses public-key cryptography to authenticate the remote computer?
Which of the following protocols uses public-key cryptography to authenticate the remote
computer?
Which of the following statements about system hardening are true?
Which of the following statements about system hardening are true?
Each correct answer represents a complete solution. Choose two.