Which of the following algorithms is found to be suitable for both digital signature and encryption?
Which of the following algorithms is found to be suitable for both digital signature and encryption?
Which of the following is responsible for maintaining certificates in a public key infrastructure (PKI)?
Which of the following is responsible for maintaining certificates in a public key infrastructure (PKI)?
Which of the following authentication methods is based on physical appearance of a user?
Which of the following authentication methods is based on physical appearance of a user?
Which of the following is a correct sequence of different layers of Open System Interconnection (OSI) model?
Which of the following is a correct sequence of different layers of Open System Interconnection
(OSI) model?
Which of the following are used to suppress gasoline and oil fires?
Which of the following are used to suppress gasoline and oil fires? Each correct answer represents a
complete solution. Choose three.
The is a simple document that provides a high-level view of the entire organization’s disaster recovery
Fill in the blank with the appropriate phrase.
The is a simple document that provides a high-level view of the entire organization’s disaster
recovery efforts.
which of the following services does the ISAKMP protocol offer to the network?
You work as a Chief Security Officer for Tech Perfect Inc. You have configured IPSec and ISAKMP
protocol in the company’s network in order to establish a secure communication infrastructure.
ccording to the Internet RFC 2408, which of the following services does the ISAKMP protocol offer to
the network?
Each correct answer represents a part of the solution. Choose all that apply.
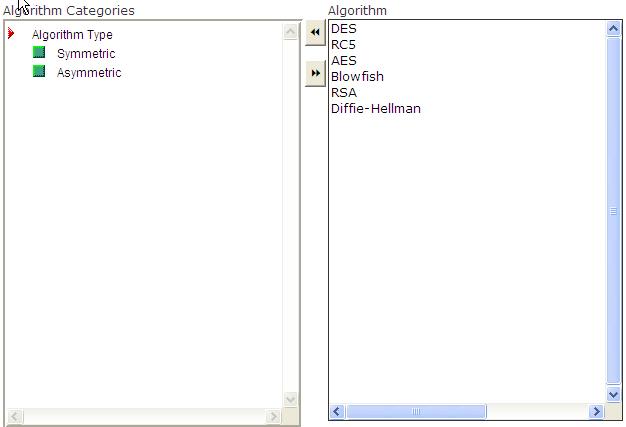
Place the encryption algorithms in their respective categories.
Which of the following methods offers a number of modeling practices and disciplines that contribute to a succ
Which of the following methods offers a number of modeling practices and disciplines that
contribute to a successful service-oriented life cycle management and modeling?
Which of the following components does the PKI use to list those certificates that have been revoked or are no
The Public Key Infrastructure (PKI) is a set of hardware, software, people, policies, and procedures
needed to create, manage, distribute, use, store, and revoke digital certificates. Which of the
following components does the PKI use to list those certificates that have been revoked or are no
longer valid?