Which of the following refers to a location away from the computer center where document copies and backup med
Which of the following refers to a location away from the computer center where document copies
and backup media are kept?
Which of the following encryption methods does the SSL protocol use in order to provide communication privacy,
Which of the following encryption methods does the SSL protocol use in order to provide
communication privacy, authentication, and message integrity? Each correct answer represents a
part of the solution. Choose two.
Which of the following will you configure on the network to perform the given task?
You work as a Network Consultant. A company named Tech Perfect Inc. hires you for security
reasons. The manager of the company tells you to establish connectivity between clients and servers
of the network which prevents eavesdropping and tampering of data on the Internet. Which of the
following will you configure on the network to perform the given task?
Which of the following techniques is he performing to accomplish his task?
John used to work as a Network Administrator for We-are-secure Inc. Now he has resigned from the
company for personal reasons. He wants to send out some secret information of the company. To do
so, he takes an image file and simply uses a tool image hide and embeds the secret file within an
image file of the famous actress, Jennifer Lopez, and sends it to his Yahoo mail id. Since he is using
the image file to send the data, the mail server of his company is unable to filter this mail. Which of
the following techniques is he performing to accomplish his task?
Which of the following intrusion detection systems (IDS) monitors network traffic and compares it against an e
Which of the following intrusion detection systems (IDS) monitors network traffic and compares it
against an established baseline?
Which of the following are the initial steps required to perform a risk analysis process?
Which of the following are the initial steps required to perform a risk analysis process? Each correct
answer represents a part of the solution. Choose three.
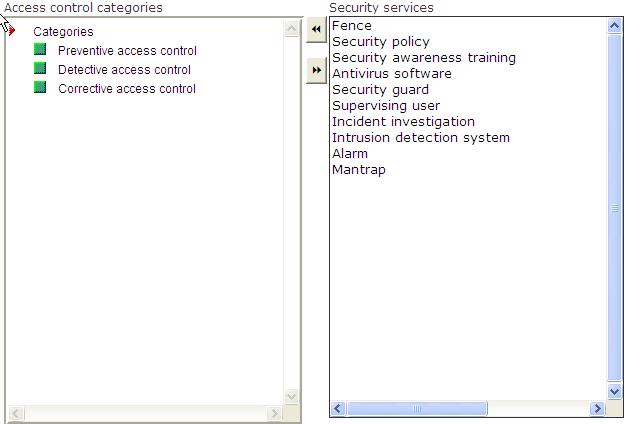
Place the appropriate security services in their corresponding categories.
Which of the following protocols uses the Internet key Exchange (IKE) protocol to set up security associations
Which of the following protocols uses the Internet key Exchange (IKE) protocol to set up security
associations (SA)?
Which of the following encryption methods will he use?
Sam is creating an e-commerce site. He wants a simple security solution that does not require each
customer to have an individual key. Which of the following encryption methods will he use?
Which of the following processes fulfills the above requirements?
An organization wants to allow a certificate authority to gain access to the encrypted data and
create digital signatures on behalf of the user. The data is encrypted using the public key from a
user’s certificate. Which of the following processes fulfills the above requirements?