Which of the following explains why record destruction requirements are included in a data retention policy?
Which of the following explains why record destruction requirements are included in a data
retention policy?
What should happen when an emergency change to a system must be performed?
What should happen when an emergency change to a system must be performed?
Which of the following is the BEST approach to take in order to effectively incorporate the concepts of busine
Which of the following is the BEST approach to take in order to effectively incorporate the concepts
of business continuity into the organization?
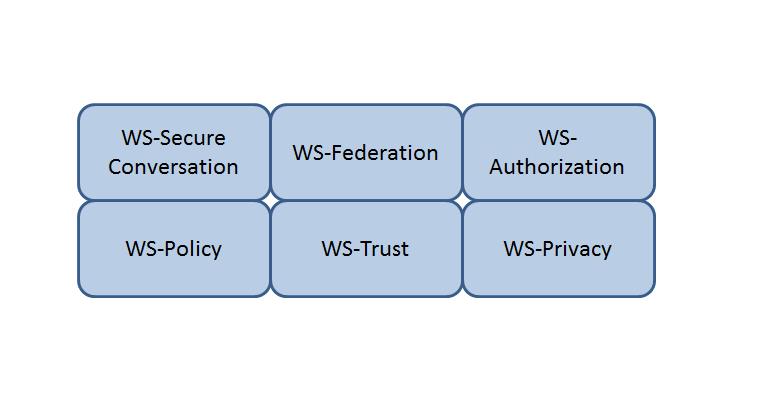
Which Web Services Security (WS-Security) specification maintains a single authenticated identity across multi
Which of the following has the GREATEST impact on an organization’s security posture?
Which of the following has the GREATEST impact on an organization’s security posture?
which of the following standards would BEST reduce the potential for data breaches?
The application of which of the following standards would BEST reduce the potential for data
breaches?
In order for a security policy to be effective within an organization, it MUST include
In order for a security policy to be effective within an organization, it MUST include
which of the following MUST be configured to only allow read access?
To protect auditable information, which of the following MUST be configured to only allow read
access?
Which of the following roles has the obligation to ensure that a third party provider…?
Which of the following roles has the obligation to ensure that a third party provider is capable of
processing and handling data in a secure manner and meeting the standards set by the organization?
What type of encryption is used to protect sensitive data in transit over a network?
What type of encryption is used to protect sensitive data in transit over a network?