what privacy principle?
A mobile device application that restricts the storage of user information to just that which is
needed to accomplish lawful business goals adheres to what privacy principle?
Which of the following is the PRIMARY benefit of implementing data-in-use controls?
Which of the following is the PRIMARY benefit of implementing data-in-use controls?
Which of the following is the organization’s MOST secure solution for protection of data?
A health care provider is considering Internet access for their employees and patients. Which of the
following is the organization’s MOST secure solution for protection of data?
Which of the following BEST describes the purpose of the security functional requirements of Common Criteria?
Which of the following BEST describes the purpose of the security functional requirements of
Common Criteria?
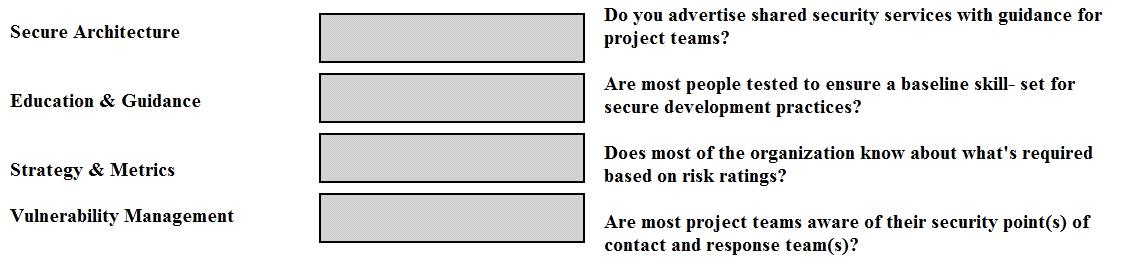
Match the objectives to the assessment questions in the governance domain of…
which of the following Institute of Electrical and Electronics Engineers (IEEE) standards will prevent an unau
Application of which of the following Institute of Electrical and Electronics Engineers (IEEE) standards
will prevent an unauthorized wireless device from being attached to a network?
The PRIMARY security concern for handheld devices is the
The PRIMARY security concern for handheld devices is the
Which of the following is the BIGGEST weakness when using native Lightweight Directory Access Protocol (LDAP)
Which of the following is the BIGGEST weakness when using native Lightweight Directory Access
Protocol (LDAP) for authentication?
The PRIMARY advantage of this implementation is
A global organization wants to implement hardware tokens as part of a multifactor authentication
solution for remote access. The PRIMARY advantage of this implementation is
Which of the following could elicit a Denial of Service (DoS) attack against a credential management system?
Which of the following could elicit a Denial of Service (DoS) attack against a credential management
system?