Changes to a Trusted Computing Base (TCB) system that could impact the security posture of that system and tri
Changes to a Trusted Computing Base (TCB) system that could impact the security posture of that
system and trigger a recertification activity are documented in the
Disaster Recovery Plan (DRP) training material should be
Disaster Recovery Plan (DRP) training material should be
The MAIN reason an organization conducts a security authorization process is to
The MAIN reason an organization conducts a security authorization process is to
What is the best approach for the CISO?
During the risk assessment phase of the project the CISO discovered that a college within the
University is collecting Protected Health Information (PHI) data via an application that was
developed in-house. The college collecting this data is fully aware of the regulations for Health
Insurance Portability and Accountability Act (HIPAA) and is fully compliant.
What is the best approach for the CISO?
During the risk assessment phase of the project the CISO discovered that a college within the
University is collecting Protected Health Information (PHI) data via an application that was
developed in-house. The college collecting this data is fully aware of the regulations for Health
Insurance Portability and Accountability Act (HIPAA) and is fully compliant.
What is the best approach for the CISO?
The World Trade Organization’s (WTO) agreement on Trade-Related Aspects of Intellectual Property Rights
The World Trade Organization’s (WTO) agreement on Trade-Related Aspects of Intellectual Property
Rights (TRIPS) requires authors of computer software to be given the
What is the best approach for the CISO?
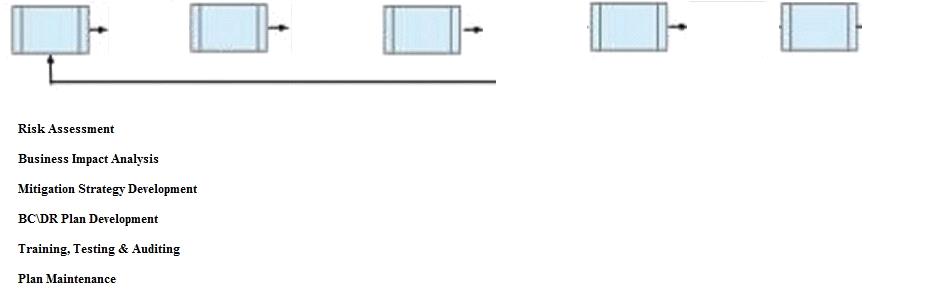
DRAG DROP
During the risk assessment phase of the project the CISO discovered that a college within the
University is collecting Protected Health Information (PHI) data via an application that was
developed in-house. The college collecting this data is fully aware of the regulations for Health
Insurance Portability and Accountability Act (HIPAA) and is fully compliant.
What is the best approach for the CISO?
Below are the common phases to creating a Business Continuity/Disaster Recovery (BC/DR) plan.
Drag the remaining BC\\DR phases to the appropriate corresponding location.
Which of the following is not a common firewall function?
Which of the following is not a common firewall function?
What is the GREATEST challenge to identifying data leaks?
What is the GREATEST challenge to identifying data leaks?
What policy should be updated to address this problem?
While investigating a malicious event, only six days of audit logs from the last month were available.
What policy should be updated to address this problem?
Who is ultimately responsible to ensure that information assets are categorized and adequate measures are take
Who is ultimately responsible to ensure that information assets are categorized and adequate
measures are taken to protect them?