What is the MOST critical factor to achieve the goals of a security program?
What is the MOST critical factor to achieve the goals of a security program?
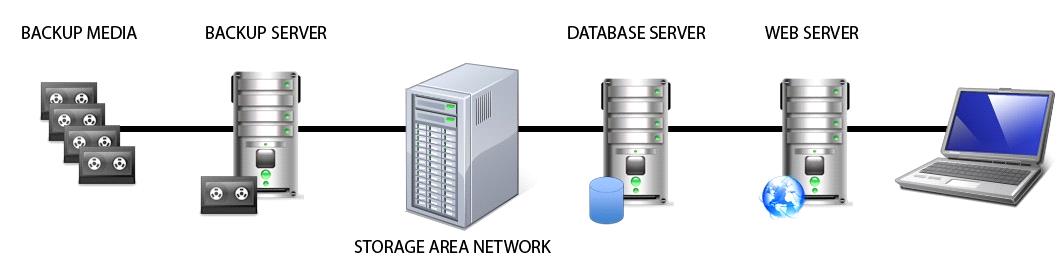
What components are in the scope of PCI-DSS?
A business has implemented Payment Card Industry Data Security Standard (PCI-DSS) compliant
handheld credit card processing on their Wireless Local Area Network (WLAN) topology.
The network team partitioned the WLAN to create a private segment for credit card processing using
a firewall to control device access and route traffic to the card processor on the Internet. What
components are in the scope of PCI-DSS?
Which of the following is the MOST appropriate action to take?
During an audit, the auditor finds evidence of potentially illegal activity. Which of the following is the
MOST appropriate action to take?
Identify the component that MOST likely lacks digital accountability related to information access.
Which of the following secure startup mechanisms are PRIMARILY designed to thwart attacks?
Which of the following secure startup mechanisms are PRIMARILY designed to thwart attacks?
Place the following information classification steps in sequential order.
What is the BEST first step for determining if the appropriate security controls are in place for protecting d
What is the BEST first step for determining if the appropriate security controls are in place for
protecting data at rest?
Which of the following provides the MOST protection against data theft of sensitive information when a laptop
Which of the following provides the MOST protection against data theft of sensitive information
when a laptop is stolen?
Which of the following is a process within a Systems Engineering Life Cycle (SELC) stage?
Which of the following is a process within a Systems Engineering Life Cycle (SELC) stage?
What component of a web application that stores the session state in a cookie can be bypassed by an attacker?
What component of a web application that stores the session state in a cookie can be bypassed by
an attacker?