Which of the following will indicate where the IT budget is BEST allocated during this time?
Refer to the information below to answer the question.
An organization experiencing a negative financial impact is forced to reduce budgets and the number
of Information Technology (IT) operations staff performing basic logical access security
administration functions. Security processes have been tightly integrated into normal IT operations
and are not separate and distinct roles.
Which of the following will indicate where the IT budget is BEST allocated during this time?
which of the following is MOST important to monitor?
Refer to the information below to answer the question.
An organization experiencing a negative financial impact is forced to reduce budgets and the number
of Information Technology (IT) operations staff performing basic logical access security
administration functions. Security processes have been tightly integrated into normal IT operations
and are not separate and distinct roles.
When determining appropriate resource allocation, which of the following is MOST important to
monitor?
Which of the following is true according to the star property (*property)?
Refer to the information below to answer the question.
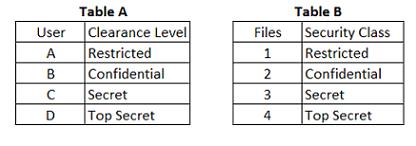
In a Multilevel Security (MLS) system, the following sensitivity labels are used in increasing levels of
sensitivity: restricted, confidential, secret, top secret. Table A lists the clearance levels for four users,
while Table B lists the security classes of four different files.
Which of the following is true according to the star property (*property)?
which user cannot write to File 3?
Refer to the information below to answer the question.In a Multilevel Security (MLS) system, the following sensitivity labels are used in increasing levels of
sensitivity: restricted, confidential, secret, top secret. Table A lists the clearance levels for four users,
while Table B lists the security classes of four different files.
In a Bell-LaPadula system, which user cannot write to File 3?
which user has the MOST restrictions when writing data to any of the four files?
Refer to the information below to answer the question.
In a Multilevel Security (MLS) system, the following sensitivity labels are used in increasing levels of
sensitivity: restricted, confidential, secret, top secret. Table A lists the clearance levels for four users,
while Table B lists the security classes of four different files.
In a Bell-LaPadula system, which user has the MOST restrictions when writing data to any of the four
files?
what is the MOST LIKELY security issue with degaussing?
Refer to the information below to answer the question.
Desktop computers in an organization were sanitized for re-use in an equivalent security
environment. The data was destroyed in accordance with organizational policy and all marking andother external indications of the sensitivity of the data that was formerly stored on the magnetic
drives were removed.
After magnetic drives were degaussed twice according to the product manufacturer’s directions,
what is the MOST LIKELY security issue with degaussing?
Which destruction method below provides the BEST assurance that the data has been removed?
Refer to the information below to answer the question.
Desktop computers in an organization were sanitized for re-use in an equivalent security
environment. The data was destroyed in accordance with organizational policy and all marking and
other external indications of the sensitivity of the data that was formerly stored on the magnetic
drives were removed.
Organizational policy requires the deletion of user data from Personal Digital Assistant (PDA) devices
before disposal. It may not be possible to delete the user data if the device is malfunctioning. Which
destruction method below provides the BEST assurance that the data has been removed?
The third party needs to have
Refer to the information below to answer the question.
A large, multinational organization has decided to outsource a portion of their Information
Technology (IT) organization to a third-party provider’s facility. This provider will be responsible for
the design, development, testing, and support of several critical, customer-based applications used
by the organization.
The third party needs to have
The organization should ensure that the third party’s physical security controls are in place so that th
Refer to the information below to answer the question.
A large, multinational organization has decided to outsource a portion of their Information
Technology (IT) organization to a third-party provider’s facility. This provider will be responsible forthe design, development, testing, and support of several critical, customer-based applications used
by the organization.
The organization should ensure that the third party’s physical security controls are in place so that
they
What additional considerations are there if the third party is located in a different country?
Refer to the information below to answer the question.
A large, multinational organization has decided to outsource a portion of their Information
Technology (IT) organization to a third-party provider’s facility. This provider will be responsible for
the design, development, testing, and support of several critical, customer-based applications used
by the organization.
What additional considerations are there if the third party is located in a different country?