Which of the following is a valid reason a customer transaction is kept beyond…?
An online retail company has formulated a record retention schedule for customer transactions.
Which of the following is a valid reason a customer transaction is kept beyond the retention
schedule?
Which of the following is the MAIN goal of a data retention policy?
Which of the following is the MAIN goal of a data retention policy?
Which of the following problems is not addressed by using OAuth (Open Standard to Authorization) 2.0 to integr
Which of the following problems is not addressed by using OAuth (Open Standard to Authorization)
2.0 to integrate a third-party identity provider for a service?
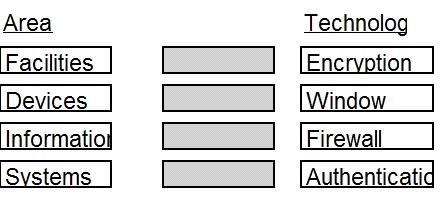
Given the various means to protect physical and logical assets, match the access management…
what type of security control?
The use of proximity card to gain access to a building is an example of what type of security control?
Which of the following is a correct list of password attacks?
Multi-Factor Authentication (MFA) is necessary in many systems given common types of password
attacks. Which of the following is a correct list of password attacks?
Which of the following is an example of two-factor authentication?
Which of the following is an example of two-factor authentication?
Which item below is a federated identity standard?
Which item below is a federated identity standard?
Which of the following could have MOST likely prevented the Peer-toPeer (P2P) program from being installed on
Refer to the information below to answer the question.
A new employee is given a laptop computer with full administrator access. This employee does not
have a personal computer at home and has a child that uses the computer to send and receive email, search the web, and use instant messaging. The organization’s Information Technology (IT)
department discovers that a peer-to-peer program has been installed on the computer using the
employee’s access.
Which of the following could have MOST likely prevented the Peer-toPeer (P2P) program from being installed on the computer?
What is a common challenge when implementing Security Assertion Markup Language…?
What is a common challenge when implementing Security Assertion Markup Language (SAML) for
identity integration between on-premise environment and an external identity provider service?