Which access control method allows the data owner (the …
Which access control method allows the data owner (the person who created the file) to control access to the
information they own?
which is described as such?
Of the seven types of Access Control Categories, which is described as such?
Designed to specify rules of acceptable behavior in the organization.
Example: Policy stating that employees may not spend time on social media websites
Data which is properly secured and can be described with terms…?
Data which is properly secured and can be described with terms like genuine or not corrupted from the original
refers to data that has a high level of what?
How can you BEST explain this?
You wish to make use of “port knocking” technologies. How can you BEST explain this?
Which of the following attack is also known as Time of …
Which of the following attack is also known as Time of Check(TOC)/Time of Use(TOU)?
Which of the following service is a distributed databas…
Which of the following service is a distributed database that translate host name to IP address to IP address to
host name?
How many bits is the address space reserved for the sou…
How many bits is the address space reserved for the source IP address within an IPv6 header?
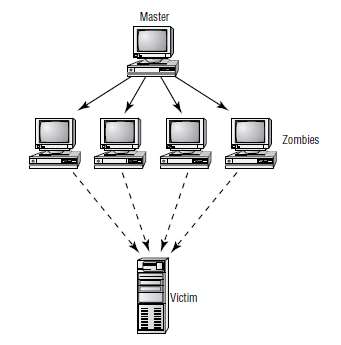
View the image below and identify the attack
The spoofed IP address used by the attacker as the sour…
What sort of attack is described by the following: An attacker has a list of broadcast addresses which it stores
into an array, the attacker sends a spoofed icmp echo request to each of those addresses in series and starts
again. The spoofed IP address used by the attacker as the source of the packets is the target/victim IP
address.
What protocol was used here to conduct the file transfer?
You are using an open source packet analyzer called Wireshark and are sifting through the various
conversations to see if anything appears to be out of order.
You are observing a UDP conversation between a host and a router. It was a file transfer between the two on
port 69. What protocol was used here to conduct the file transfer?