What method might an IS auditor utilize to test wireles…
What method might an IS auditor utilize to test wireless security at branch office locations?
Which of the following is the MOST important action in …
Which of the following is the MOST important action in recovering from a cyberattack?
Which of the following is BEST suited for secure commun…
Which of the following is BEST suited for secure communications within a small group?
which of the following would make wireless local area n…
Disabling which of the following would make wireless local area networks more secure against
unauthorized access?
Which of the following cryptographic systems is MOST ap…
Which of the following cryptographic systems is MOST appropriate for bulk data encryption and
small devices such as smart cards?
An efficient use of public key infrastructure (PKI) sho…
An efficient use of public key infrastructure (PKI) should encrypt the:
Which of the following ensures a sender’s authenticity …
Which of the following ensures a sender’s authenticity and an e-mail’s confidentiality?
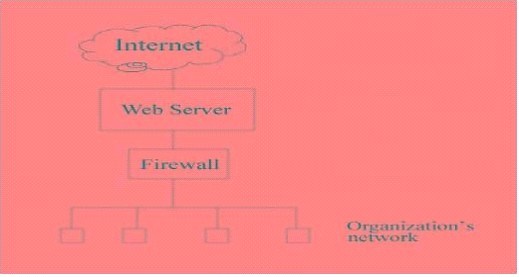
To detect attack attempts that the firewall is unable t…
Which of the following should be a concern to an IS aud…
Which of the following should be a concern to an IS auditor reviewing a wireless network?
what aspect of an authorized honeypot?
An IS auditor should be MOST concerned with what aspect of an authorized honeypot?