Why is BIG-IP ASM ideally suited to protect against lay…
Why is BIG-IP ASM ideally suited to protect against layer 7 attacks, including HTTP and HTTPS/SSL traffic, when compared to an intrusion prevention system
(IPS)?
Which aspect of F5’s Intelligent Services Platform help…
Which aspect of F5’s Intelligent Services Platform helps you extend your security conversation to include F5 professionals and customers?
what would you use to supplement the Visual Policy Editor?
If your customer has a policy requirement that cannot be handled in the Visual Policy Editor, what would you use to supplement the Visual Policy Editor?
Using the………….feature in GTM, F5’s Application …
Select the best word or phrase to complete the following sentence.
Using the………….feature in GTM, F5’s Application Delivery
Firewall solution can handle a significantly higher number of queries than traditional
DNS servers.
Even though F5 is an application delivery controller, i…
Even though F5 is an application delivery controller, it can also effectively mitigate attacks directed at the network layer.
service can incorporate dynamic lists of threatening IP…
Complete the statement below by choosing the correct word or phrase to complete the sentence.
By identifying IP addresses and security categories associated with malicious activity, the BIG-IP………….. service can incorporate dynamic lists of threatening IP
addresses into the BIG-IP platform, adding context to policy decisions.
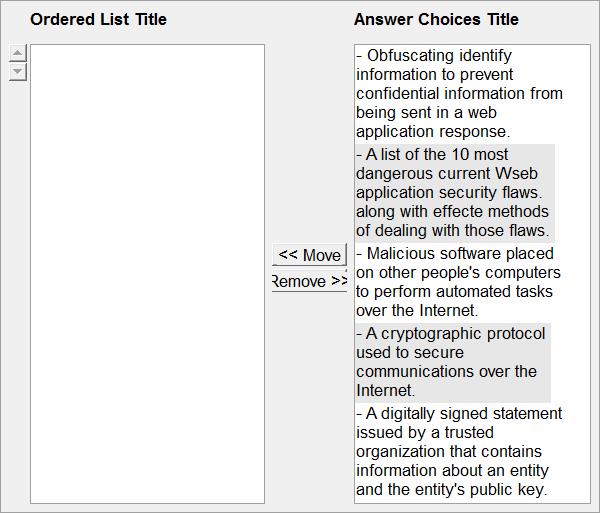
Content scrubbing Build List and Reorder:
What are the other consequences to a business as a resu…
When a business is hacked, they often lose more than money. What are the other consequences to a business as a result of being hacked?
Select two.
Select the key question you would use to ask your custo…
Select the key question you would use to ask your customer related to DNS attacks?
What feature of the F5 Exchange solution helps administ…
What feature of the F5 Exchange solution helps administrators to streamline implementation for added security and granular control?