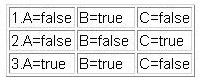
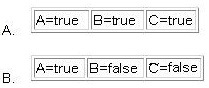
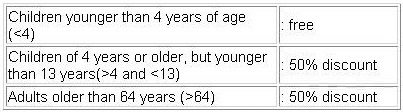Which test situation is missing if the coverage type decision points modified condition/decision coverage is u
What does RFC 791 specify the standards for?
You are introducing a co-worker to the security systems in place in your organization. During the
discussion you begin talking about the network, and how it is implemented. You mention
something in RFC 791, and are asked what that is. What does RFC 791 specify the standards for?
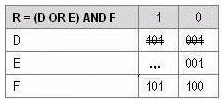
Which values are missing where the dots are stated (? to make the table complete?
What wireless standard allows for up to 11 Mbps transmission rates and operates in the 2.4GHz range?
You have been given the task of building the new wireless networks for your office, and you need
to verify that your equipment will not interfere with other wireless equipment frequencies. What
wireless standard allows for up to 11 Mbps transmission rates and operates in the 2.4GHz range?
How many equivalence classes can be distinguished from the above specification?
what is the type and subtype for an 802.11 authentication packet?
When performing wireless network traffic analysis, what is the type and subtype for an 802.11
authentication packet?
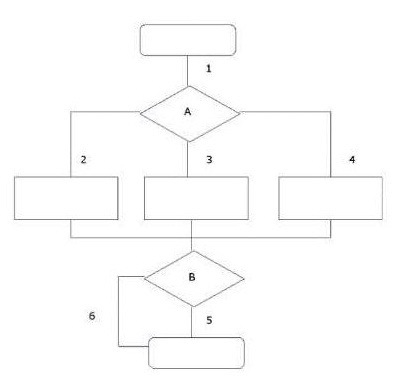
Which step is ?stablishing the starting point?
The specification of test cases according to a test design technique follows five general steps.
Which step is stablishing the starting point?Which step is ?stablishing the starting point?
Which of the following Snort rules will log any tcp traffic from any host other than 172.16.40.50 using any po
You are configuring your new IDS machine, where you have recently installed Snort. While you
are working with this machine, you wish to create some basic rules to test the ability to log traffic
as you desire. Which of the following Snort rules will log any tcp traffic from any host other than
172.16.40.50 using any port, to any host in the 10.0.10.0/24 network using any port?
Which test situations can be differentiated when the coverage type paths test depth level 2 is used?
Which four of the following are the primary parts of the Snort configuration file?
You are configuring a new IDS, running Snort, in your network. To better configure Snort, you are
studying the configuration file. Which four of the following are the primary parts of the Snort
configuration file?