Which defect has an internal cause that can be solved within the test team?
Which defect has an internal cause that can be solved within the test team?
what type of WLAN is this frame a part of?
If you capture an 802.11 frame, and the ToDS bit is set to zero and the FromDS bit is set to zero,
what type of WLAN is this frame a part of?
which circumstance can Exploratory Testing be used effectively?
Under which circumstance can Exploratory Testing be used effectively?
What transmission system uses short bursts combined together as a channel?
There are several options available to you for your new wireless networking technologies, and you
are examining how different systems function. What transmission system uses short bursts
combined together as a channel?
What is not an advantage of applying a test design technique and recording it in the test specifications?
What is not an advantage of applying a test design technique and recording it in the test
specifications?
What is a reason an IDS cannot manage hardware failures?
You have just installed a new Intrusion Detection System in your network. You are concerned that
there are functions this system will not be able to perform. What is a reason an IDS cannot
manage hardware failures?
Where must the ‘bullets’ for test case 4 be placed?
See the illustration below:
To test a registration application for a weekend trip, logical test cases must be created in
accordance with the Data Combination Test. In addition, it has been agreed that less depth testing
must be performed. One data pair has been defined that must be fully tested in combination:
* car – attraction
Eight test cases are designed using a classification tree.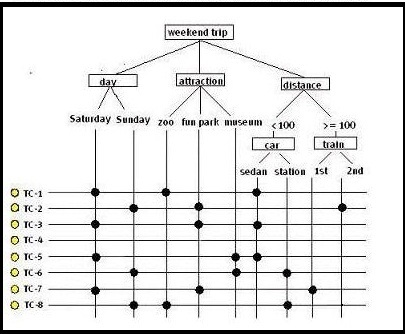
Where must the ‘bullets’ for test case 4 be placed?
Which keyword is used to tell Snort to ignore a defined number of bytes before looking inside the packet for a
For the new Snort rules you are building, it will be required to have Snort examine inside the
content of the packet. Which keyword is used to tell Snort to ignore a defined number of bytes
before looking inside the packet for a content match?
What is the fourth characteristic?
A structured testing approach is characterized by:
* providing concrete footholds
* covering the full scope and describing the complete range of relevant aspects
* providing a structure, so that it is clear what exactly by whom, when and in what sequence has to
be done
What is the fourth characteristic?
What is the function of this rule?
You have recently taken over the security of a mid-sized network. You are reviewing the current
configuration of the IPTables firewall, and notice the following rule:
ipchains -A input -p TCP -d 0.0.0.0/0 12345 -j DENY
What is the function of this rule?

