what algorithm?
What type of cryptographic system is represented in this image?
What classic cipher is shown in this image?
Which of the following answers is the word SECURITY after having been encrypted using the following Polybius C
Packets received by Node 10, and sent from Node 7 will reveal which of the following combination of source IP
The exhibit represents a simple routed network. Node 7 is a Windows 2000 Professional machine
that establishes a TCP communication with Node 10, a Windows 2003 Server. The routers are
Cisco 2500 series running IOS 11.2.
While working at Node 10, you run a packet capture. Packets received by Node 10, and sent from
Node 7 will reveal which of the following combination of source IP and source Physical addresses: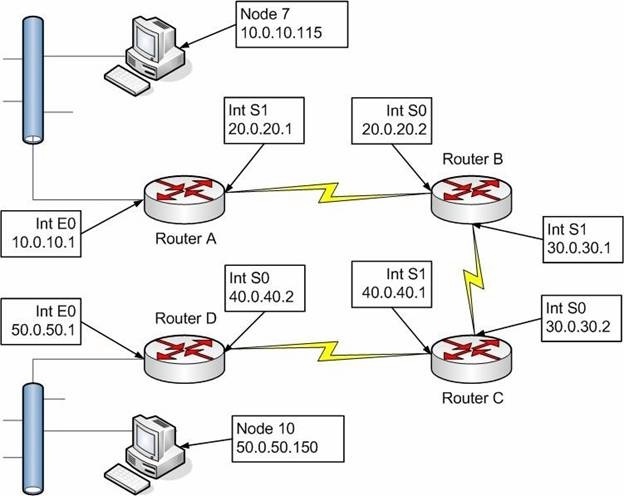
which of the following statements are true about your network traffic?
You have implemented an IPSec policy, using only AH. You are analyzing your network traffic in
Network Monitor, which of the following statements are true about your network traffic?
which test level is this the definition?
See the definition below:
Tests in which the supplying party demonstrates that the product particularly meets the functional
and non-functional specifications and the technical design, among other things.
Of which test level is this the definition?
what must first be installed?
In order to perform promiscuous mode captures using the Wireshark capture tool on a Windows
Server
2003 machine, what must first be installed?
which Map phase activity does the pre-test take place?
In which Map phase activity does the pre-test take place?
What is the IP address range reserved for internal use for APIPA in Microsoft networks?
You are configuring the rules on your firewall, and need to take into consideration that some
clients in the
network are using automatic addressing. What is the IP address range reserved for internal use
for APIPA in Microsoft networks?





