What setting must Willem adjust to ensure that user accounts must be manually reset by him when they are locke
Willem is the network administrator for his company, a toy manufacturing company in London. Willem manages the entire company�s network which consists of one Server 2003 Active Directory domain. Willem was hired on last month to replace the last administrator that retired. To Willem�s amazement, the company previously had no password policies in place. The CIO has just recently created new network policies which include a comprehensive password policy. This new password policy states that every password setting in group policy must be set. After implementing this new policy, many users are calling Willem and stating that they locked themselves out of their accounts. The CIO�s policy states that once a user locks him or herself out, they must wait a period of time until that account is unlocked. Willem has convinced the CIO to let him change that specific password policy so that Willem must manually unlock user accounts when they call. What setting must Willem adjust to ensure that user accounts must be manually reset by him when they are locked out?
In Buffer Overflow exploit, which of the following registers gets overwritten with return address of the explo
In Buffer Overflow exploit, which of the following registers gets overwritten with return address of the exploit code?
Identify the line in the source code that might lead to buffer overflow?
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server in your organization. They notice that there is excessive number of functions in the source code that might lead to buffer overflow. These C++ functions do not check bounds. Identify the line in the source code that might lead to buffer overflow?
How can an attacker disguise his buffer overflow attack signature such that there is a greater probability of
Basically, there are two approaches to network intrusion detection: signature detection, and anomaly detection. The signature detection approach utilizes well-known signatures for network traffic to identify potentially malicious traffic. The anomaly detection approach utilizes a previous history of network traffic to search for patterns that are abnormal, which would indicate an intrusion. How can an attacker disguise his buffer overflow attack signature such that there is a greater probability of his attack going undetected by the IDS?
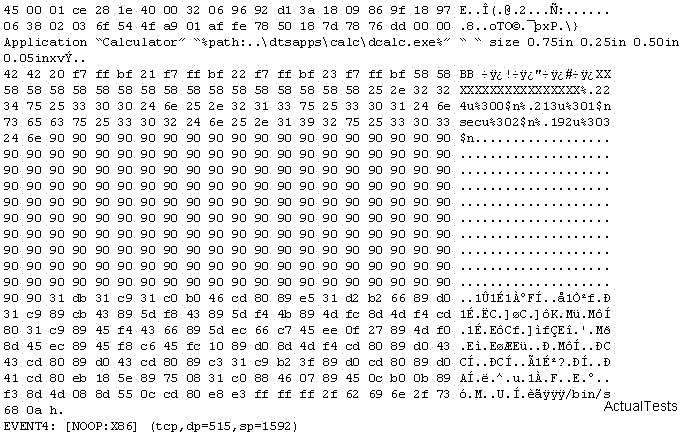
an analyst what would you conclude about the attack?
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack. You also notice “/bin/sh” in the ASCII part of the output. As an analyst what would you conclude about the attack?