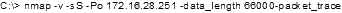What will the following command accomplish?
What are the security risks of running a "repair" installation for Windows XP?
What are the security risks of running a “repair” installation for Windows XP?
What tool could you use to get this information?
You are the security analyst working for a private company out of France. Your current assignment
is to obtain credit card information from a Swiss bank owned by that company. After initial
reconnaissance, you discover that the bank security defenses are very strong and would take too
long to penetrate. You decide to get the information by monitoring the traffic between the bank and
one of its subsidiaries in London. After monitoring some of the traffic, you see a lot of FTP packets
traveling back and forth. You want to sniff the traffic and extract usernames and passwords. What
tool could you use to get this information?
What filter should George use in Ethereal?
George is the network administrator of a large Internet company on the west coast. Per corporate
policy, none of the employees in the company are allowed to use FTP or SFTP programs without
obtaining approval from the IT department. Few managers are using SFTP program on their
computers. Before talking to his boss, George wants to have some proof of their activity.
George wants to use Ethereal to monitor network traffic, but only SFTP traffic to and from his
network. What filter should George use in Ethereal?
What type of firewall must you implement to abide by this policy?
You are assisting a Department of Defense contract company to become compliant with the
stringent security policies set by the DoD. One such strict rule is that firewalls must only allow
incoming connections that were first initiated by internal computers. What type of firewall must you
implement to abide by this policy?
What type of virus is this that you are testing?
You are running known exploits against your network to test for possible vulnerabilities. To test the
strength of your virus software, you load a test network to mimic your production network. Your
software successfully blocks some simple macro and encrypted viruses. You decide to really test
the software by using virus code where the code rewrites itself entirely and the signatures change
from child to child, but the functionality stays the same. What type of virus is this that you are
testing?
What will the other routers communicate between themselves?
In a virtual test environment, Michael is testing the strength and security of BGP using multiple
routers to mimic the backbone of the Internet. This project will help him write his doctoral thesis on
“bringing down the Internet”. Without sniffing the traffic between the routers, Michael sends
millions of RESET packets to the routers in an attempt to shut one or all of them down. After a few
hours, one of the routers finally shuts itself down. What will the other routers communicate
between themselves?
What is the following command trying to accomplish?
Which feature will you disable to eliminate the ability to enumerate this information on your Cisco routers?
Your company uses Cisco routers exclusively throughout the network. After securing the routers to
the best of your knowledge, an outside security firm is brought in to assess the network security.
Although they found very few issues, they were able to enumerate the model, OS version, and
capabilities for all your Cisco routers with very little effort. Which feature will you disable to
eliminate the ability to enumerate this information on your Cisco routers?
Why would a scanner like Nessus is not recommended in this situation?
George is performing security analysis for Hammond and Sons LLC. He is testing security
vulnerabilities of their wireless network. He plans on remaining as “stealthy” as possible during the
scan. Why would a scanner like Nessus is not recommended in this situation?