How many exits should Steven include in his design for the computer forensics lab?
Steven has been given the task of designing a computer forensics lab for the company he works for. He has found documentation on all aspects of how to design a lab except the number of exits needed.
How many exits should Steven include in his design for the computer forensics lab?
What type of removable media could the investigator use?
A forensics investigator needs to copy data from a computer to some type of removable media so he can examine the information at another location. The problem is that the data is around 42GB in size.
What type of removable media could the investigator use?
What crime should Julie focus on?
Julie is a college student majoring in Information Systems and Computer Science. She is currently writing an essay for her computer crimes class. Julie paper focuses on white-collar crimes in America and how forensics investigators investigate the cases.
What crime should Julie focus on?
What type of flash memory card comes in either Type I or Type II and consumes only five percent of the power r
What type of flash memory card comes in either Type I or Type II and consumes only five percent of the power required by small hard drives?
With the standard Linux second extended file system (Ext2fs), a file is deleted when the inode internal link c
With the standard Linux second extended file system (Ext2fs), a file is deleted when the inode internal link count reaches ______
0 IP addresses signify?
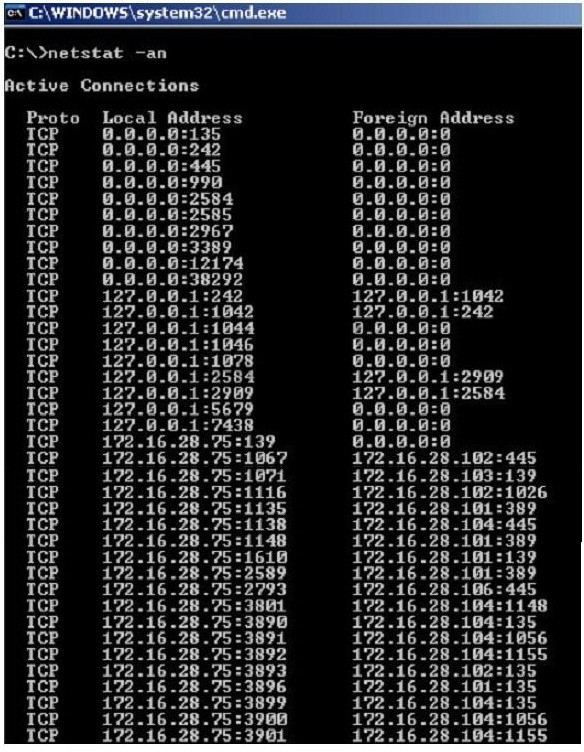
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus.
He runs the netstat command on the machine to see its current connections.
In the following screenshot, what do the 0.0.0.0 IP addresses signify?
what should be searched to find a JPEG file in hexadecimal format?
When searching through file headers for picture file formats, what should be searched to find a JPEG file in hexadecimal format?
When the case is brought to court, whom should the prosecuting attorney call upon for not upholding company po
Davidson Trucking is a small transportation company that has three local offices in Detroit Michigan. Ten female employees that work for the company have gone to an attorney reporting that male employees repeatedly harassed them and that management did nothing to stop the problem. Davidson has employee policies that outline all company guidelines, including awareness on harassment and how it will not be tolerated.
When the case is brought to court, whom should the prosecuting attorney call upon for not upholding company policy?
What happens when a file is deleted by a Microsoft operating system using the FAT file system?
What happens when a file is deleted by a Microsoft operating system using the FAT file system?
what layer does a cross site scripting attack occur on?
At what layer does a cross site scripting attack occur on?