One way to identify the presence of hidden partitions on a suspect hard drive is to:
One way to identify the presence of hidden partitions on a suspect hard drive is to:
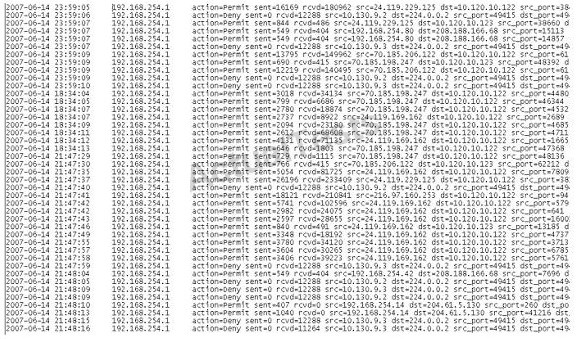
What can the investigator infer from the screenshot seen below?
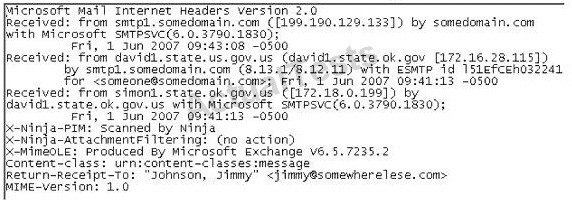
where did the email first originate from?
If you discover a criminal act while investigating a corporate policy abuse, it becomes a public- sector inves
If you discover a criminal act while investigating a corporate policy abuse, it becomes a public- sector investigation and should be referred to law enforcement?
What will the following command accomplish in Linux?
What will the following command accomplish in Linux?
fdisk /dev/hda
What is the name of the standard Linux command that can be used to create bit-stream images?
What is the name of the standard Linux command that can be used to create bit-stream images?
What can the investigator do to prove the violation?
A suspect is accused of violating the acceptable use of computing resources, as he has visited adult websites and downloaded images. The investigator wants to demonstrate that the suspect did indeed visit these sites. However, the suspect has cleared the search history and emptied the cookie cache. Moreover, he has removed any images he might have downloaded.
What can the investigator do to prove the violation? Choose the most feasible option.
What would this attack on the company? PBX system be called?
Cylie is investigating a network breach at a state organization in Florida. She discovers that the intruders were able to gain access into the company firewalls by overloading them with IP packets.
Cylie then discovers through her investigation that the intruders hacked into the company phone system and used the hard drives on their PBX system to store shared music files.
What would this attack on the company? PBX system be called?
What can you do to prove that the evidence is the same as it was when it first entered the lab?
You are assigned to work in the computer forensics lab of a state police agency. While working on a high profile criminal case, you have followed every applicable procedure, however your boss is still concerned that the defense attorney might question wheather evidence has been changed while at the lab.
What can you do to prove that the evidence is the same as it was when it first entered the lab?
What type of analysis helps to identify the time and sequence of events in an investigation?
What type of analysis helps to identify the time and sequence of events in an investigation?