what field would she be considered an expert in?
While presenting his case to the court, Simon calls many witnesses to the stand to testify. Simon decides to call Hillary Taft, a lay witness, to the stand.
Since Hillary is a lay witness, what field would she be considered an expert in?
What does this indicate on the computer?
While searching through a computer under investigation, you discover numerous files that appear to have had the first letter of the file name replaced by the hex code byte 5h.
What does this indicate on the computer?
What method would be most efficient for you to acquire digital evidence from this network?
You are contracted to work as a computer forensics investigator for a regional bank that has four 30 TB storage area networks that store customer data.
What method would be most efficient for you to acquire digital evidence from this network?
What area of the law is the employee violating?
You are working for a large clothing manufacturer as a computer forensics investigator and are called in to investigate an unusual case of an employee possibly stealing clothing designs from the company and selling them under a different brand name for a different company.
What you discover during the course of the investigation is that the clothing designs are actually original products of the employee and the company has no policy against an employee selling his own designs on his own time.
The only thing that you can find that the employee is doing wrong is that his clothing design incorporates the same graphic symbol as that of the company with only the wording in the graphic being different.
What area of the law is the employee violating?
Where is the startup configuration located on a router?
Where is the startup configuration located on a router?
What is considered a grant of a property right given to an individual who discovers or invents a new machine,
What is considered a grant of a property right given to an individual who discovers or invents a new machine, process, useful composition of matter or manufacture?
What term should Harold use?
Harold is finishing up a report on a case of network intrusion, corporate spying, and embezzlement that he has been working on for over six months.
He is trying to find the right term to use in his report to describe network-enabled spying.
What term should Harold use?
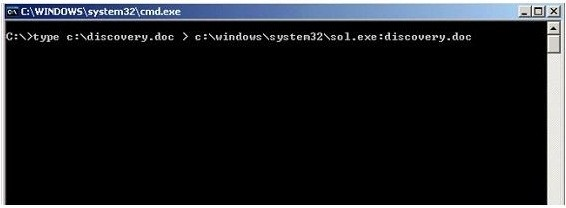
What feature of Windows is the following command trying to utilize?
Why would a company issue a dongle with the software they sell?
Why would a company issue a dongle with the software they sell?
What technique this user was trying?
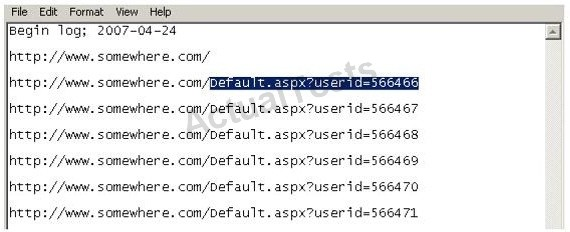
Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd.
From the log, the investigator can see where the person in question went on the Internet.
From the log, it appears that the user was manually typing in different user ID numbers.
What technique this user was trying?