What can a pen tester do to detect input sanitization issues?
Black-box testing is a method of software testing that examines the functionality of an
application (e.g. what the software does) without peering into its internal structures or
workings. Black-box testing is used to detect issues in SQL statements and to detect SQL
injection vulnerabilities.
Most commonly, SQL injection vulnerabilities are a result of coding vulnerabilities during the
Implementation/Development phase and will likely require code changes.
Pen testers need to perform this testing during the development phase to find and fix the
SQL injection vulnerability.
What can a pen tester do to detect input sanitization issues?
Which of the following is NOT related to the Internal Security Assessment penetration testing strategy?
Which of the following is NOT related to the Internal Security Assessment penetration testing
strategy?
What are placeholders (or markers) in an HTML document that the web server will dynamically replace with data
What are placeholders (or markers) in an HTML document that the web server will
dynamically replace with data just before sending the requested documents to a browser?
Which of the following techniques do attackers use to create backdoors to covertly gather critical information
Attackers create secret accounts and gain illegal access to resources using backdoor while
bypassing the authentication procedures. Creating a backdoor is a where an attacker
obtains remote access to a computer on a network.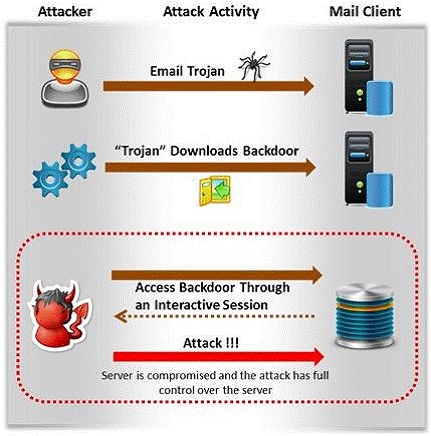
Which of the following techniques do attackers use to create backdoors to covertly gather
critical information about a target machine?
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides toplevel guidance for conducting the penetration testing.
Various factors are considered while preparing the scope of ROE which clearly explain the
limits associated with the security test.
Which of the following factors is NOT considered while preparing the scope of the Rules of
Engagment (ROE)?
Which of the following protocols cannot be used to filter VoIP traffic?
Which of the following protocols cannot be used to filter VoIP traffic?
which phase(s)?
Identify the type of testing that is carried out without giving any information to the employees or administra
Identify the type of testing that is carried out without giving any information to the employees
or administrative head of the organization.




